Caisse d’Epargne – Disponibilité des fonds
Vérifiez en temps réel la disponibilité des fonds sur le compte d'un client
Comment réduire son risque d'impayé ?
Ce service permet de vérifier la disponibilité des fonds pour le compte de notre client pour un montant donné d’une transaction.
Un client porteur de votre carte de crédit privative effectue une transaction sur un site d’e-commerce avec celle-ci. Le client a donné, au préalable, une délégation à votre établissement, ainsi qu’un consentement explicite à son teneur de compte dans lequel est domicilié le prélèvement de la carte.
Via cette API « disponibilité des fonds » mise à disposition par la banque, vous pouvez demander en temps réel la confirmation que le client ait suffisamment de fonds sur son compte pour couvrir le montant de cette transaction SANS lui demander ses identifiants de connexion en ligne, réduisant de fait votre exposition au risque d’impayé.
Le teneur de comptes répond positivement ou négativement sans aucun blocage de fonds correspondant au montant de la transaction, ni validation de celle-ci.
Les ressources de cette API ne peuvent être consommées que par des prestataires ayant le rôle d’émetteurs d’instruments de paiement liés à une carte (« CBPII » ou « PIISP » suivant la version STET), ce prérequis étant décrit dans voir la section « Éligibilité ».
Une fois les prérequis remplis, le processus global est le suivant :
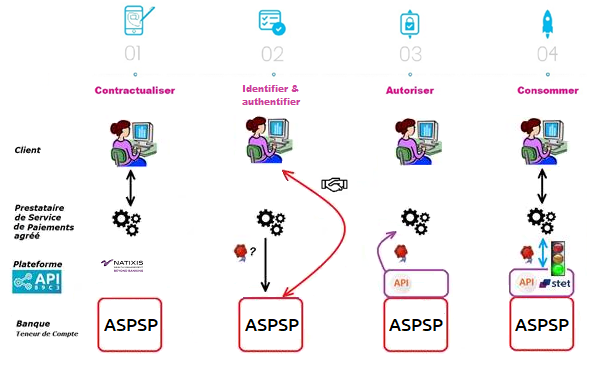
1- Vous avez établi un contrat avec le client et lui délivrez une carte avec prélèvement domicilié chez le teneur de compte. Il vous l’indique à travers vos interfaces.
2- Lors du premier échange avec les infrastructures du teneur de compte, vous allez faire une demande de jeton d’autorisation (et un jeton de rafraichissement). Le principe de base est, qu’en tant que TPP CBPII, vous devez obtenir ces jetons AVANT de consommer les ressources de l’API. Ce jeton est généré par le teneur de compte (ASPSP) APRES avoir identifié et authentifié le client.
En tant que teneur de compte, nous allons :
- vérifier vos certificats et agréments ;
- et via le jeu de la redirection, nous allons identifier et authentifier fortement le client afin de récupérer son consentement et de générer le jeton d’accès.
3- Si l’autorisation est accordée par le client, vous pourrez ensuite récupérer un jeton d’accès OAUTH2 (et son jeton de rafraichissement) via des échanges sécurisés avec la plateforme BPCE API (voir le cas d’usage « Récupérez votre jeton d’accès !« ).
4- En présentant ce jeton d’autorisation valable 180 jours, vous pourrez alors consommer les ressources de l’API « disponibilité des fonds » et réduire votre risque d’impayé en interrogeant la banque sur l’existence de la provision sur le compte du client correspondant au montant du paiement (voir le cas d’usage « Consommez et vérifiez la disponibilité des fonds ! »).
Au bout du délai réglementaire de 180 jours, ce processus devra être reconduit (voir le cas d’usage « Rafraichissez votre jeton !« ).
NB : le gestionnaire de compte ASPSP a possibilité de vous refuser l’accès pour différents motifs justifiés (API non conforme, compte bloqué entre-temps, etc..).
Récupérer votre jeton
L’accès aux API « information sur compte » ou « disponibilité des fonds » vous est autorisé via un jeton d’accès (access_token) qui peut être obtenu en appliquant le standard de place OAUTH2.
Cinématique de récupération du jeton d’autorisation
1. Notre client (PSU) vous indique l’identité de son établissement de compte.
2. Vous initiez la séquence de récupération du jeton d’accès OAuth2 en redirigeant le client (PSU), via son navigateur internet, vers l’infrastructure informatique d’autorisation de l’établissement teneur de compte (ASPSP) et en utilisant la commande : GET /authorize
Voir aussi la spécification de place STET V1.4.0.47 / Part I / section 3.4.3.2 / page 21
3. Le teneur de compte (ASPSP) va :
- Identifier et authentifier son client par l’une des méthodes d’authentification forte qu’elle propose et qu’il présente au client ;
- Effectuer des vérifications liées à votre profil en tant qu’AISP ou CBPII (validité de vos certificats QWAC et QSEALC et de votre rôle, non révocation de votre profil, etc.)
4. Une fois ces vérifications effectuées et si elles sont concluantes, l’établissement bancaire va rediriger le client (PSU) vers votre site en utilisant votre URL de « call-back » (redirection) que vous nous aurez transmise lors du processus de « Go Live ».
En effet, l’AISP doit préciser pour son APP consommatrice, une URL qui sera appelée par l’établissement bancaire :
- Si le PSU a autorisé la récupération de ses données par l’AISP
- Ou en cas de refus du consentement
- Ou si la cinématique d’identification et d’authentification est interrompue à l’une de ses étapes (exemple : timeout sur l’écran d’identification ou sur l’écran d’authentification forte).
Si le PSU vous a autorisé à récupérer ses données chez son teneur de compte, vous trouverez dans la réponse à cet appel un code à utilisation unique qui a une durée de vie courte.
5. Via un appel de type POST /token, vous allez pouvoir alors demander directement au teneur de compte votre jeton d’accès OAUTH2 (access_token) avec les éléments reçus précédemment dont le code à utilisation unique.
NB : les requêtes /token du flow Authorization Code doivent être envoyée SANS le paramètre « scope ».
Voir aussi la spécification de place STET V1.4.0.47 / Part I / section 3.4.3.2 / page 22
6. L’établissement teneur de compte (ASPSP) va :
- Effectuer des vérifications liées à votre profil en tant qu’AISP ou CBPII (validité des certificats et de votre agrément, non révocation de votre profil, etc.)
- Vous identifier et vous authentifier en tant qu’AISP ou CBPII via votre certificat que vous mettrez à disposition pour sécuriser l’échange mutuel.
7. Une fois ces vérifications effectuées et si elles sont concluantes, le teneur de compte va vous renvoyer une réponse HTTP200 (OK) contenant, entres autres, le jeton d’accès OAUTH2 (access_token).
Voir aussi la spécification de place STET V1.4.0.47 / Part I / section 3.4.3.2 / page 23
8. Dès que le jeton d’accès OAUTH2 (access_token) délivré par la banque a été récupéré par vos soins, vous pourrez le présenter pour pouvoir consommer les ressources de l’API.
Ce jeton est accompagné d’un refresh_token valable 180 jours que vous devez conserver. Lorsque votre access_token arrive à expiration, vous pouvez en redemander un nouveau en suivant la rubrique « Vue d’ensemble » > « Rafraîchir votre jeton« .
Au bout de 180 jours votre refresh_token arrive à expiration. Pour en récupérer un nouveau, vous devrez reprendre cette cinématique « Récupérer votre jeton » et passer, de facto, par une nouvelle étape d’authentification forte du client auprès de son établissement bancaire (cf. point 3. ci-dessus).
Pour plus de détails, voir aussi OAUTH 2.0 Authorization Framework : https://tools.ietf.org/html/rfc6749#section-4.1
Exemple
Un exemple de requête est fourni dans la rubrique « Comment tester l’API ? » > « Assemblage sandbox« .
Rafraîchir votre jeton
Principe
Les jetons OAUTH2 ayant une durée de vie limitée, il vous est nécessaire d’en demander le rafraîchissement avant son expiration.
Règles de base
Le teneur de compte (ASPSP) dispose au plus d’un jeton d’accès (access_token) et d’un jeton de rafraîchissement (refresh_token) valides par triplet client PSU / TPP / rôle AISP ou CBPII.
- Le jeton d’accès a une durée de validité courte (de l’ordre d’une heure max) sur un périphérique ou une application de notre client
- Le jeton de rafraîchissement a une durée de vie de 180 jours
- Le jeton de rafraîchissement et le jeton d’accès doivent pouvoir être révoqués à tout moment
- Si le jeton d’accès est révoqué alors le jeton de rafraîchissement doit l’être aussi et réciproquement
Cinématique du rafraîchissement de votre jeton d’accès (access_token)
1. Vous demandez le renouvellement du jeton d’accès auprès de l’ASPSP
2. L’ASPSP initie le renouvellement du jeton d’accès
3. L’ASPSP récupère le certificat du TPP auprès du référentiel de place
4. L’ASPSP contrôle la validité et la non révocation du certificat présenté
5. L’ASPSP contrôle la date de la dernière authentification (< 180 jours)
6. L’ASPSP vous transmet le nouveau jeton d’accès et l’ancien jeton de rafraîchissement
7. Vous stockez le jeton d’autorisation et l’ancien jeton de rafraîchissement de façon sûre
8. L’ASPSP invalide l’ancien jeton d’autorisation
Exemple
Un exemple de requête est fourni dans la rubrique « Comment tester l’API ? » > « Assemblage sandbox« .
Publications réglementaires
| Période | Document |
| Disponibilité des API DSP2 à date | Télécharger le document |
| Statistiques T1 2025 | Télécharger le document |
| Statistiques T4 2024 | Télécharger le document |
| Statistiques T3 2024 | Télécharger le document |
| Statistiques T2 2024 | Télécharger le document |
| Statistiques T1 2024 | Télécharger le document |
| Statistiques T4 2023 | Télécharger le document |
| Statistiques T3 2023 | Télécharger le document |
| Statistiques T2 2023 | Télécharger le document |
| Statistiques T1 2023 | Télécharger le document |
| Statistiques T4 2022 | Télécharger le document |
| Statistiques T3 2022 | Télécharger le document |
| Statistiques T2 2022 | Télécharger le document |
| Statistiques T1 2022 | Télécharger le document |
| Statistiques T4 2021 | Télécharger le document |
| Statistiques T3 2021 | Télécharger le document |
| Statistiques T2 2021 | Télécharger le document |
| Statistiques T1 2021 | Télécharger le document |
| Statistiques T4 2020 | Télécharger le document |
| Statistiques T3 2020 | Télécharger le document |
| Statistiques T2 2020 | Télécharger le document |
| Statistiques T1 2020 | Télécharger le document |
Catégories
-
STETPSD2 V1.4.0
-
STETPSD2V142
-
STETPSD2V162
- get accountsBalances
- get accounts
- get accountsOverdrafts
- get accountsOwners
- get accountsTransactionsDetails
- get accountsTransactions
- put consents
- get endUserIdentity
- post fundsConfirmations
- post paymentRequestConfirmation
- put paymentRequest
- get paymentRequestTransactions
- get paymentRequests
- post paymentRequests
- get trustedBeneficiaries
/stet/psd2/v1/accounts/{accountResourceId}/balances
accountsBalances
Résumé
Retrieval of an account balances report (AISP)
Description
Description
This call returns a set of balances for a given PSU account that is specified by the AISP through an account resource Identification
- The ASPSP must provide at least the accounting balance on the account.
- The ASPSP can provide other balance restitutions, e.g. instant balance, as well, if possible.
- Actually, from the PSD2 perspective, any other balances that are provided through the Web-Banking service of the ASPSP must also be provided by this ASPSP through the API.
Prerequisites
- The TPP has been registered by the Registration Authority for the AISP role
- The TPP and the PSU have a contract that has been enrolled by the ASPSP
- At this step, the ASPSP has delivered an OAUTH2 “Authorization Code” or “Resource Owner Password” access token to the TPP (cf. § 3.4.2).
- The TPP and the ASPSP have successfully processed a mutual check and authentication
- The TPP has presented its OAUTH2 “Authorization Code” or “Resource Owner Password” access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) if any.
- The ASPSP takes into account the access token that establishes the link between the PSU and the AISP.
- The TPP has previously retrieved the list of available accounts for the PSU
Business flow
The AISP requests the ASPSP on one of the PSU’s accounts. The ASPSP answers by providing a list of balances on this account.
- The ASPSP must provide at least the accounting balance on the account.
- The ASPSP can provide other balance restitutions, e.g. instant balance, as well, if possible.
- Actually, from the PSD2 perspective, any other balances that are provided through the Web-Banking service of the ASPSP must also be provided by this ASPSP through the API.
Scopes
- aisp
- piisp
- extended_transaction_history
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| accountResourceId (required) | string path Identification of account resource to fetch |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header http-signature of the request (cf. https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 200 | The ASPSP answers with a list of account balances |
| 204 | No Content |
| 400 | Bad Request |
| 401 | Unauthorized |
| 403 | Forbidden |
| 404 | Not Found |
| 405 | Method Not Allowed |
| 406 | Not Acceptable |
| 408 | Request Timeout |
| 429 | Too Many Requests |
| 500 | Internal Server Error |
| 503 | Service Unavailable |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1/accounts
accounts
Résumé
Retrieval of the PSU accounts (AISP)
Description
Description
This call returns all payment accounts that are relevant the PSU on behalf of whom the AISP is connected. Thanks to HYPERMEDIA, each account is returned with the links aiming to ease access to the relevant transactions and balances. The result may be subject to pagination (i.e. retrieving a partial result in case of having too many results) through a set of pages by the ASPSP. Thereafter, the AISP may ask for the first, next, previous or last page of results.
Prerequisites
- The TPP has been registered by the Registration Authority for the AISP role.
- The TPP and the PSU have a contract that has been enrolled by the ASPSP
- At this step, the ASPSP has delivered an OAUTH2 « Authorization Code » or « Resource Owner Password » access token to the TPP (cf. § 3.4.2).
- The TPP and the ASPSP have successfully processed a mutual check and authentication
- The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) if any.
- The ASPSP takes into account the access token that establishes the link between the PSU and the AISP.
Business Flow
The TPP sends a request to the ASPSP for retrieving the list of the PSU payment accounts. The ASPSP computes the relevant PSU accounts and builds the answer as an accounts list. The result may be subject to pagination in order to avoid an excessive result set. Each payment account will be provided with its characteristics.
Scopes
- aisp
- extended_transaction_history
- piisp
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header http-signature of the request (cf. https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 200 | The ASPSP return a PSU context – listing the accounts that have been made available to the AISP by the PSU and, – for each of these accounts, the further transactions that have been enabled by the PSU through HYPERMEDIA links. |
| 204 | No Content |
| 401 | Unauthorized |
| 403 | Forbidden |
| 404 | Not Found |
| 405 | Method Not Allowed |
| 406 | Not Acceptable |
| 408 | Request Timeout |
| 429 | Too Many Requests |
| 500 | Internal Server Error |
| 503 | Service Unavailable |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1/accounts/{accountResourceId}/transactions
accountsTransactions
Résumé
Retrieval of an account transaction set (AISP)
Description
Description
This call returns transactions for an account for a given PSU account that is specified by the AISP through an account resource identification. The request may use some filter parameter in order to restrict the query
- on a given imputation date range
- past a given incremental technical identification
The result may be subject to pagination (i.e. retrieving a partial result in case of having too many results) through a set of pages by the ASPSP. Thereafter, the AISP may ask for the first, next, previous or last page of results.
Prerequisites
- The TPP has been registered by the Registration Authority for the AISP role
- The TPP and the PSU have a contract that has been enrolled by the ASPSP
- At this step, the ASPSP has delivered an OAUTH2 « Authorization Code » or « Resource Owner Password » access token to the TPP (cf. § 3.4.2).
- The TPP and the ASPSP have successfully processed a mutual check and authentication
- The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) is any.
- The ASPSP takes into account the access token that establishes the link between the PSU and the AISP.
- The TPP has previously retrieved the list of available accounts for the PSU
Business flow
The AISP requests the ASPSP on one of the PSU’s accounts. It may specify some selection criteria. The ASPSP answers by a set of transactions that matches the query. The result may be subject to pagination in order to avoid an excessive result set.
Scopes
- aisp
- extended_transaction_history
- piisp
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| accountResourceId (required) | string path Identification of account resource to fetch |
| dateFrom | string query Inclusive minimal imputation date of the transactions. Transactions having an imputation date equal to this parameter are included within the result. |
| dateTo | string query Exclusive maximal imputation date of the transactions. Transactions having an imputation date equal to this parameter are not included within the result. |
| afterEntryReference | string query Specifies the value on which the result has to be computed. Only the transaction having a technical identification greater than this value must be included within the result |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header http-signature of the request (cf. https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 200 | Complete transactions response |
| 204 | No Content |
| 400 | Bad Request |
| 401 | Unauthorized |
| 403 | Forbidden |
| 404 | Not Found |
| 405 | Method Not Allowed |
| 406 | Not Acceptable |
| 408 | Request Timeout |
| 429 | Too Many Requests |
| 500 | Internal Server Error |
| 503 | Service Unavailable |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1/consents
consents
Résumé
Forwarding the PSU consent (AISP)
Description
Description
In the mixed detailed consent on accounts
- the AISP captures the consent of the PSU
- then it forwards this consent to the ASPSP
This consent replaces any prior consent that was previously sent by the AISP.
Prerequisites
- The TPP has been registered by the Registration Authority for the AISP role.
- The TPP and the PSU have a contract that has been enrolled by the ASPSP
- At this step, the ASPSP has delivered an OAUTH2 « Authorization Code » or « Resource Owner Password » access token to the TPP (cf. § 3.4.2).
- The TPP and the ASPSP have successfully processed a mutual check and authentication
- The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) if any.
- The ASPSP takes into account the access token that establishes the link between the PSU and the AISP.
Business Flow
The PSU specifies to the AISP which of his/her accounts will be accessible and which functionalities should be available. The AISP forwards these settings to the ASPSP. The ASPSP answers by HTTP201 return code.
Scopes
- aisp
- piisp
- extended_transaction_history
Paramètres
| access (required) | AccessRequestResource body parameters of a access request |
| Authorization (required) | string header Access token to be passed as a header |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header http-signature of the request (cf. https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 201 | Created |
| 400 | Bad Request |
| 401 | Unauthorized |
| 403 | Forbidden |
| 405 | Method Not Allowed |
| 406 | Not Acceptable |
| 408 | Request Timeout |
| 429 | Too Many Requests |
| 500 | Internal Server Error |
| 503 | Service Unavailable |
Entrées
application/json
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1/funds-confirmations
fundsConfirmations
Résumé
Payment coverage check request (PIISP)
Description
Description
The PIISP can ask an ASPSP to check if a given amount can be covered by the liquidity that is available on a PSU cash account or payment card.
Prerequisites
- The TPP has been registered by the Registration Authority for the PIISP role
- The TPP and the PSU have a contract that has been registered by the ASPSP
- At this step, the ASPSP has delivered an « Authorization Code », a « Resource Owner Password » or a « Client Credential » OAUTH2 access token to the TPP (cf. § 3.4.2).
- Each ASPSP has to implement either the « Authorization Code »/ »Resource Owner Password » or the « Client Credential » OAUTH2 access token model.
- Doing this, it will edit the [security] section on this path in order to specify which model it has chosen
- The TPP and the ASPSP have successfully processed a mutual check and authentication
- The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU.
Business flow
The PIISP requests the ASPSP for a payment coverage check against either a bank account or a card primary identifier.
The ASPSP answers with a structure embedding the original request and the result as a Boolean.
Scopes
- extended_transaction_history
- piisp
- aisp
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| paymentCoverage (required) | PaymentCoverageRequestResource body parameters of a payment coverage request |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header http-signature of the request (cf. https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 200 | payment coverage request |
| 400 | Bad Request |
| 401 | Unauthorized |
| 403 | Forbidden |
| 405 | Method Not Allowed |
| 406 | Not Acceptable |
| 408 | Request Timeout |
| 429 | Too Many Requests |
| 500 | Internal Server Error |
| 503 | Service Unavailable |
Entrées
application/json
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1/trusted-beneficiaries
trustedBeneficiaries
Résumé
Retrieval of the trusted beneficiaries list (AISP)
Description
Description
This call returns all trusted beneficiaries that have been set by the PSU. Those beneficiaries can benefit from an SCA exemption during payment initiation. The result may be subject to pagination (i.e. retrieving a partial result in case of having too many results) through a set of pages by the ASPSP. Thereafter, the AISP may ask for the first, next, previous or last page of results.
Prerequisites
- The TPP has been registered by the Registration Authority for the AISP role.
- The TPP and the PSU have a contract that has been enrolled by the ASPSP
- At this step, the ASPSP has delivered an OAUTH2 « Authorization Code » or « Resource Owner Password » access token to the TPP (cf. § 3.4.2).
- The TPP and the ASPSP have successfully processed a mutual check and authentication
- The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) if any.
- The ASPSP takes into account the access token that establishes the link between the PSU and the AISP.
Business Flow
The AISP asks for the trusted beneficiaries list. The ASPSP answers with a list of beneficiary details structure.
Scopes
- piisp
- extended_transaction_history
- aisp
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header http-signature of the request (cf. https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 200 | The ASPSP returns the list of whitelisted beneficiaries |
| 204 | No Content |
| 401 | Unauthorized |
| 403 | Forbidden |
| 404 | Not Found |
| 405 | Method Not Allowed |
| 406 | Not Acceptable |
| 429 | Too Many Requests |
| 500 | Internal Server Error |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.4.2/accounts/{accountResourceId}/balances
accountsBalances
Résumé
Retrieval of an account balances report (AISP)
Description
This call returns a set of balances for a given PSU account that is specified by the AISP through an account resource Identification
– The TPP has been registered by the Registration Authority for the AISP role
– The TPP and the PSU have a contract that has been enrolled by the ASPSP – At this step, the ASPSP has delivered an OAUTH2 “Authorization Code” or “Resource Owner Password” access token to the TPP (cf. § 3.4.2).
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP has presented its OAUTH2 “Authorization Code” or “Resource Owner Password” access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) if any.
– The ASPSP takes into account the access token that establishes the link between the PSU and the AISP.
– The TPP has previously retrieved the list of available accounts for the PSU
The AISP requests the ASPSP on one of the PSU’s accounts.
The ASPSP answers by providing a list of balances on this account. – The ASPSP must provide at least the accounting balance on the account. – The ASPSP can provide other balance restitutions, e.g. instant balance, as well, if possible. – Actually, from the PSD2 perspective, any other balances that are provided through the Web-Banking service of the ASPSP must also be provided by this ASPSP through the API.
Scopes
- cbpii
- aisp
- extended_transaction_history
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| accountResourceId (required) | string path Identification of account resource to fetch |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 200 | The ASPSP answers with a list of account balances |
| 204 | No content. |
| 400 | Invalid status value |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 404 | Not found, no request available. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 503 | Service unavailable. |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.4.2/accounts
accounts
Résumé
Retrieval of the PSU accounts (AISP)
Description
This call returns all payment accounts that are relevant the PSU on behalf of whom the AISP is connected.
Thanks to HYPERMEDIA, each account is returned with the links aiming to ease access to the relevant transactions and balances.
The result may be subject to pagination (i.e. retrieving a partial result in case of having too many results) through a set of pages by the ASPSP. Thereafter, the AISP may ask for the first, next, previous or last page of results. – The TPP has been registered by the Registration Authority for the AISP role.
– The TPP and the PSU have a contract that has been enrolled by the ASPSP – At this step, the ASPSP has delivered an OAUTH2 « Authorization Code » or « Resource Owner Password » access token to the TPP (cf. § 3.4.2).
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) if any.
– The ASPSP takes into account the access token that establishes the link between the PSU and the AISP. The TPP sends a request to the ASPSP for retrieving the list of the PSU payment accounts.
The ASPSP computes the relevant PSU accounts and builds the answer as an accounts list. The result may be subject to pagination in order to avoid an excessive result set. Each payment account will be provided with its characteristics.
Scopes
- extended_transaction_history
- cbpii
- aisp
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 200 | The ASPSP return a PSU context – listing the accounts that have been made available to the AISP by the PSU and, – for each of these accounts, the further transactions that have been enabled by the PSU through HYPERMEDIA links. |
| 204 | No content. |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 404 | Not found, no request available. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 503 | Service unavailable. |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.4.2/accounts/{accountResourceId}/transactions
accountsTransactions
Résumé
Retrieval of an account transaction set (AISP)
Description
This call returns transactions for an account for a given PSU account that is specified by the AISP through an account resource identification.
The request may use some filter parameter in order to restrict the query – on a given imputation date range – past a given incremental technical identification
The result may be subject to pagination (i.e. retrieving a partial result in case of having too many results) through a set of pages by the ASPSP. Thereafter, the AISP may ask for the first, next, previous or last page of results.
– The TPP has been registered by the Registration Authority for the AISP role
– The TPP and the PSU have a contract that has been enrolled by the ASPSP – At this step, the ASPSP has delivered an OAUTH2 « Authorization Code » or « Resource Owner Password » access token to the TPP (cf. § 3.4.2).
– The TPP and the ASPSP have successfully processed a mutual check and authentication – The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) is any.
– The ASPSP takes into account the access token that establishes the link between the PSU and the AISP.
– The TPP has previously retrieved the list of available accounts for the PSU
The AISP requests the ASPSP on one of the PSU’s accounts. It may specify some selection criteria.
The ASPSP answers by a set of transactions that matches the query. The result may be subject to pagination in order to avoid an excessive result set.
The default transaction set, in the absence of filter query parameter, has to be specified and documented by the implementation.
Scopes
- aisp
- cbpii
- extended_transaction_history
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| accountResourceId (required) | string path Identification of account resource to fetch |
| dateFrom | string query Inclusive minimal imputation date of the transactions. Transactions having an imputation date equal to this parameter are included within the result. |
| dateTo | string query Exclusive maximal imputation date of the transactions. Transactions having an imputation date equal to this parameter are not included within the result. |
| entryReferenceFrom | string query Specifies the value on which the result has to be computed. Only the transaction having a technical identification greater than this value must be included within the result |
| entryReferenceto | string query Specifies the value on which the result has to be computed. Only the transaction having a technical identification less than or equal to this value must be included within the result |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 200 | Complete transactions response |
| 204 | No content. |
| 400 | Invalid status value |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 404 | Not found, no request available. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 503 | Service unavailable. |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.4.2/consents
consents
Résumé
Forwarding the PSU consent (AISP)
Description
In the mixed detailed consent on accounts
– the AISP captures the consent of the PSU
– then it forwards this consent to the ASPSP
This consent replaces any prior consent that was previously sent by the AISP.
– The TPP has been registered by the Registration Authority for the AISP role.
– The TPP and the PSU have a contract that has been enrolled by the ASPSP – At this step, the ASPSP has delivered an OAUTH2 « Authorization Code » or « Resource Owner Password » access token to the TPP (cf. § 3.4.2).
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) if any.
– The ASPSP takes into account the access token that establishes the link between the PSU and the AISP.
The PSU specifies to the AISP which of his/her accounts will be accessible and which functionalities should be available.
The AISP forwards these settings to the ASPSP.
The ASPSP answers by HTTP201 return code.
Scopes
- aisp
- extended_transaction_history
- cbpii
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| access (required) | Access body List of consents granted to the AISP by the PSU. |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 201 | Created |
| 400 | Invalid status value |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 501 | Not Implemented. This code should be used when the entry point is implemented but cannot provide a result, given the context. When the entry point is not implemented at all, HTTP400 will be returned. |
| 503 | Service unavailable. |
Entrées
application/json
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.4.2/end-user-identity
endUserIdentity
Résumé
Retrieval of the identity of the end-user (AISP)
Description
This call returns the identity of the PSU (end-user).
– The TPP has been registered by the Registration Authority for the AISP role.
– The TPP and the PSU have a contract that has been enrolled by the ASPSP – At this step, the ASPSP has delivered an OAUTH2 « Authorization Code » or « Resource Owner Password » access token to the TPP (cf. § 3.4.2).
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) if any.
– The ASPSP takes into account the access token that establishes the link between the PSU and the AISP. The AISP asks for the identity of the PSU. The ASPSP answers with the identity, i.e. first and last names of the end-user.
Scopes
- aisp
- extended_transaction_history
- cbpii
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 200 | The ASPSP returns the identity of the PSU |
| 204 | No content. |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 404 | Not found, no request available. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 429 | Too many requests. |
| 500 | Internal server error. |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.4.2/funds-confirmations
fundsConfirmations
Résumé
Payment coverage check request (CBPII)
Description
The CBPII can ask an ASPSP to check if a given amount can be covered by the liquidity that is available on a PSU cash account or payment card.
– The TPP has been registered by the Registration Authority for the CBPII role
– The TPP and the PSU have a contract that has been registered by the ASPSP – At this step, the ASPSP has delivered an « Authorization Code », a « Resource Owner Password » or a « Client Credential » OAUTH2 access token to the TPP (cf. § 3.4.2). – Each ASPSP has to implement either the « Authorization Code »/ »Resource Owner Password » or the « Client Credential » OAUTH2 access token model. – Doing this, it will edit the [security] section on this path in order to specify which model it has chosen
– The TPP and the ASPSP have successfully processed a mutual check and authentication – The TPP has presented its OAUTH2 « Authorization Code », « Resource Owner Password » or « Client Credential » access token which allows the ASPSP to identify the relevant PSU.
The CBPII requests the ASPSP for a payment coverage check against either a bank account or a card primary identifier.
The ASPSP answers with a structure embedding the original request and the result as a Boolean.
Scopes
- aisp
- cbpii
- extended_transaction_history
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| paymentCoverage (required) | PaymentCoverageRequestResource body parameters of a payment coverage request |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 200 | payment coverage request |
| 400 | Invalid status value |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 503 | Service unavailable. |
Entrées
application/json
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.4.2/payment-requests/{paymentRequestResourceId}/o-confirmation
paymentRequestOConfirmation
Résumé
Confirmation of a payment request or a modification request using an OAUTH2 Authorization code grant (PISP)
Description
The PISP confirms one of the following requests or modifications:
– payment request on behalf of a merchant
– transfer request on behalf of the account’s owner
– standing-order request on behalf of the account’s owner
The ASPSP answers with a status of the relevant request and the subsequent Credit Transfer. – The TPP has been registered by the Registration Authority for the PISP role
– The TPP was provided with an OAUTH2 « Client Credential » access token by the ASPSP (cf. § 3.4.2).
– The TPP has previously posted a Request which has been saved by the ASPSP (cf. § 4.5.3) – The ASPSP has answered with a location link to the saved Payment Request (cf. § 4.5.4) – The TPP has retrieved the saved request in order to get the relevant resource Ids (cf. § 4.6).
– The PSU has been authenticated by the ASPSP through an OAUTH2 authorization code grant flow (REDIRECT approach) and the PISP got the relevant token
– The TPP and the ASPSP have successfully processed a mutual check and authentication – The TPP has presented its « OAUTH2 Authorization Code » access token Once the PSU has been authenticated through an OAUTH2 authorization code grant flow (REDIRECT approach), it is the due to the PISP to confirm the Request to the ASPSP in order to complete the process flow.
The ASPSP must wait for confirmation before executing the subsequent Credit Tranfer.
Scopes
- pisp
- aisp
- extended_transaction_history
- cbpii
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| paymentRequestResourceId (required) | string path Identification of the Payment Request Resource |
| confirmationRequest (required) | ConfirmationResource body Parameters needed for confirmation of the Payment Request, especially in « EMBEDDED-1-FACTOR » approach Even though there is no parameter, a Json (void) body structure must be provided. |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 200 | retrieval of the Payment Request enriched with the status report |
| 400 | Invalid status value |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 409 | Conflict. The request could not be completed due to a conflict with the current state of the target resource. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 503 | Service unavailable. |
Entrées
application/json
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.4.2/trusted-beneficiaries
trustedBeneficiaries
Résumé
Retrieval of the trusted beneficiaries list (AISP)
Description
This call returns all trusted beneficiaries that have been set by the PSU.
Those beneficiaries can benefit from an SCA exemption during payment initiation.
The result may be subject to pagination (i.e. retrieving a partial result in case of having too many results) through a set of pages by the ASPSP. Thereafter, the AISP may ask for the first, next, previous or last page of results.
– The TPP has been registered by the Registration Authority for the AISP role.
– The TPP and the PSU have a contract that has been enrolled by the ASPSP – At this step, the ASPSP has delivered an OAUTH2 « Authorization Code » or « Resource Owner Password » access token to the TPP (cf. § 3.4.2).
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) if any.
– The ASPSP takes into account the access token that establishes the link between the PSU and the AISP.
The AISP asks for the trusted beneficiaries list.
The ASPSP answers with a list of beneficiary details structure.
Scopes
- cbpii
- aisp
- extended_transaction_history
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 200 | The ASPSP returns the list of whitelisted beneficiaries |
| 204 | No content. |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 404 | Not found, no request available. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 501 | Not Implemented. This code should be used when the entry point is implemented but cannot provide a result, given the context. When the entry point is not implemented at all, HTTP400 will be returned. |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.6.2/accounts/{accountResourceId}/balances
accountsBalances
Résumé
Retrieval of an account balances report (AISP)
Description
Description
This call returns a set of balances for a given PSU account that is specified by the AISP through an account resource Identification
Prerequisites
– The TPP was registered by the Registration Authority for the AISP role
– The TPP and the PSU have a contract that was enrolled by the ASPSP – At this step, the ASPSP has delivered an OAUTH2 « Authorization Code » or « Resource Owner Password » access token to the TPP (cf. § 3.4.2).
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) if any.
– The ASPSP takes into account the access token that establishes the link between the PSU and the AISP.
– The TPP has previously retrieved the list of available accounts for the PSU
### Business flow
The AISP requests the ASPSP on one of the PSU’s accounts.
The ASPSP answers by providing a list of balances on this account.
– The ASPSP should provide at least one balance on the account. – For cash account, this balance should be the accounting balance (CACC) – For card transactions account, the accounting balance is meaningless and must be replaced by an other type of balance (OTHR).
– Case of no registered transaction on the account, this balance will have an amount equal to zero.
– The ASPSP can provide other balance restitutions, e.g. instant balance, as well, if possible.
– Actually, from the PSD2 perspective, any other balances that are provided through the Web-Banking service of the ASPSP must also be provided by this ASPSP through the API.
Scopes
- cbpii
- extended_transaction_history
- pisp
- aisp
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| accountResourceId (required) | string path Identification of account resource to fetch |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
| workspace | string query Workspace to be used for processing an AISP request. If not provided, the default workspace is computed from the authentication that was used for getting the OAuth2 Access Token. |
Codes retour
| 200 | The ASPSP answers with a list of account balances |
| 204 | No content. |
| 400 | Invalid status value |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 404 | Not found, no request available. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 503 | Service unavailable. |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.6.2/accounts
accounts
Résumé
Retrieval of the PSU accounts (AISP)
Description
Description
This call returns all payment accounts that are relevant for the PSU on behalf of whom the AISP is connected.
Thanks to HYPERMEDIA, each account is returned with the links aiming to ease access to the relevant transactions and balances.
The result may be subject to pagination (i.e. retrieving a partial result in case of having too many results) through a set of pages by the ASPSP. Thereafter, the AISP may ask for the first, next, previous or last page of results. Prerequisites – The TPP was registered by the Registration Authority for the AISP role.
– The TPP and the PSU have a contract that was enrolled by the ASPSP – At this step, the ASPSP has delivered an OAUTH2 « Authorization Code » or « Resource Owner Password » access token to the TPP (cf. § 3.4.2).
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) if any.
– The ASPSP takes into account the access token that establishes the link between the PSU and the AISP. ### Business Flow
The TPP sends a request to the ASPSP for retrieving the list of the PSU payment accounts.
The ASPSP computes the relevant PSU accounts and builds the answer as an accounts list.
The result may be subject to pagination in order to avoid an excessive result set.
Each payment account will be provided with its characteristics.
Scopes
- aisp
- pisp
- cbpii
- extended_transaction_history
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
| workspace | string query Workspace to be used for processing an AISP request. If not provided, the default workspace is computed from the authentication that was used for getting the OAuth2 Access Token. |
Codes retour
| 200 | The ASPSP return a PSU context – listing the accounts that were made available to the AISP by the PSU and, – for each of these accounts, the further transactions that were enabled by the PSU through HYPERMEDIA links. |
| 204 | No content. |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 404 | Not found, no request available. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 503 | Service unavailable. |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.6.2/accounts/{accountResourceId}/overdrafts
accountsOverdrafts
Résumé
Retrieval of an account overdraft (AISP)
Description
Description
This call returns the overdrafts that can be used for a given PSU account that is specified by the AISP through an account resource identification.
The request may use some filter parameter in order to restrict the query
Prerequisites
– The TPP was registered by the Registration Authority for the AISP role
– The TPP and the PSU have a contract that was enrolled by the ASPSP – At this step, the ASPSP has delivered an OAUTH2 « Authorization Code » or « Resource Owner Password » access token to the TPP (cf. § 3.4.2).
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) is any.
– The ASPSP takes into account the access token that establishes the link between the PSU and the AISP.
– The TPP has previously retrieved the list of available accounts for the PSU
Business flow
The AISP requests the ASPSP on one of the PSU’s accounts.
The ASPSP answers by the overdraft that can be applied.
Scopes
- pisp
- aisp
- extended_transaction_history
- cbpii
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| accountResourceId (required) | string path Identification of account resource to fetch |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
| workspace | string query Workspace to be used for processing an AISP request. If not provided, the default workspace is computed from the authentication that was used for getting the OAuth2 Access Token. |
Codes retour
| 200 | Overdraft response |
| 204 | No content. |
| 400 | Invalid status value |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 404 | Not found, no request available. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 503 | Service unavailable. |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.6.2/accounts/{accountResourceId}/owners
accountsOwners
Résumé
Retrieval of an account owners (AISP)
Description
Description
This call returns the owners identities for a given PSU account that is specified by the AISP through an account resource identification.
This call cannot be used when the account is owned by a legal entity where the identity of this entity is directly available in the account structure (field [company]).
### Prerequisites
– The TPP was registered by the Registration Authority for the AISP role
– The TPP and the PSU have a contract that was enrolled by the ASPSP – At this step, the ASPSP has delivered an OAUTH2 « Authorization Code » or « Resource Owner Password » access token to the TPP (cf. § 3.4.2).
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) is any.
– The ASPSP takes into account the access token that establishes the link between the PSU and the AISP.
– The TPP has previously retrieved the list of available accounts for the PSU
Business flow
The AISP requests the ASPSP on one of the PSU’s accounts.
The ASPSP answers by the identities of the account owners.
Scopes
- cbpii
- aisp
- pisp
- extended_transaction_history
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| accountResourceId (required) | string path Identification of account resource to fetch |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
| workspace | string query Workspace to be used for processing an AISP request. If not provided, the default workspace is computed from the authentication that was used for getting the OAuth2 Access Token. |
Codes retour
| 200 | Account owners identities response |
| 204 | No content. |
| 400 | Invalid status value |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 404 | Not found, no request available. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 503 | Service unavailable. |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.6.2/accounts/{accountResourceId}/transactions/{transactionResourceId}/details
accountsTransactionsDetails
Résumé
Retrieval of transaction details (AISP)
Description
Description
This call returns the details of a transaction from a given PSU account.
The AISP has to specified
– the account through an account resource identification
– the transaction through a transaction resource identifcation
### Prerequisites
– The TPP was registered by the Registration Authority for the AISP role
– The TPP and the PSU have a contract that was enrolled by the ASPSP – At this step, the ASPSP has delivered an OAUTH2 « Authorization Code » or « Resource Owner Password » access token to the TPP (cf. § 3.4.2).
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) is any.
– The ASPSP takes into account the access token that establishes the link between the PSU and the AISP.
– The TPP has previously retrieved the list of available accounts for the PSU and the transactions from one given account
– A transaction includes a « details » hyperlink which indicates that detailed information is available for this transaction.
Business flow
The AISP requests the ASPSP on one of the transactions.
The ASPSP answers by the details on this transaction.
Scopes
- cbpii
- aisp
- extended_transaction_history
- pisp
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| accountResourceId (required) | string path Identification of account resource to fetch |
| transactionResourceId (required) | string path Identification of transaction resource to fetch |
| dateFrom | string query Inclusive minimal imputation date of the transactions. Transactions having an imputation date equal to this parameter are included within the result. |
| dateTo | string query Exclusive maximal imputation date of the transactions. Transactions having an imputation date equal to this parameter are not included within the result. |
| dateType | string query This parameter specifies the type of date on which [dateFrom] and [dateTo] apply. If not provided, the ASPSP will use its own default date type as specified in its implementation documentation. The implementation documentation must also specify which date types are supported. |
| entryReferenceFrom | string query Specifies the value on which the result has to be computed. Only the transaction having a technical identification greater than this value must be included within the result |
| entryReferenceto | string query Specifies the value on which the result has to be computed. Only the transaction having a technical identification less than or equal to this value must be included within the result |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
| workspace | string query Workspace to be used for processing an AISP request. If not provided, the default workspace is computed from the authentication that was used for getting the OAuth2 Access Token. |
Codes retour
| 200 | Complete transactions response |
| 204 | No content. |
| 400 | Invalid status value |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 404 | Not found, no request available. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 503 | Service unavailable. |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.6.2/accounts/{accountResourceId}/transactions
accountsTransactions
Résumé
Retrieval of an account transaction set (AISP)
Description
Description
This call returns transactions for an account for a given PSU account that is specified by the AISP through an account resource identification.
The request may use some filter parameter in order to restrict the query – on a given imputation date range – past a given incremental technical identification
The result may be subject to pagination (i.e. retrieving a partial result in case of having too many results) through a set of pages by the ASPSP. Thereafter, the AISP may ask for the first, next, previous or last page of results.
### Prerequisites
– The TPP was registered by the Registration Authority for the AISP role
– The TPP and the PSU have a contract that was enrolled by the ASPSP – At this step, the ASPSP has delivered an OAUTH2 « Authorization Code » or « Resource Owner Password » access token to the TPP (cf. § 3.4.2).
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) is any.
– The ASPSP takes into account the access token that establishes the link between the PSU and the AISP.
– The TPP has previously retrieved the list of available accounts for the PSU
### Business flow
The AISP requests the ASPSP on one of the PSU’s accounts. It may specify some selection criteria.
The ASPSP answers by a set of transactions that matches the query.
– The result may be subject to pagination in order to avoid an excessive result set.
– Case of no registered transaction on the account, this result will be an empty list.
The default transaction set, in the absence of filter query parameter, has to be specified and documented by the implementation.
The sort order of transaction might be specific to each ASPSP, due to each Information System constraints.
Scopes
- pisp
- cbpii
- aisp
- extended_transaction_history
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| accountResourceId (required) | string path Identification of account resource to fetch |
| dateFrom | string query Inclusive minimal imputation date of the transactions. Transactions having an imputation date equal to this parameter are included within the result. |
| dateTo | string query Exclusive maximal imputation date of the transactions. Transactions having an imputation date equal to this parameter are not included within the result. |
| dateType | string query This parameter specifies the type of date on which [dateFrom] and [dateTo] apply. If not provided, the ASPSP will use its own default date type as specified in its implementation documentation. The implementation documentation must also specify which date types are supported. |
| entryReferenceFrom | string query Specifies the value on which the result has to be computed. Only the transaction having a technical identification greater than this value must be included within the result |
| entryReferenceto | string query Specifies the value on which the result has to be computed. Only the transaction having a technical identification less than or equal to this value must be included within the result |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
| workspace | string query Workspace to be used for processing an AISP request. If not provided, the default workspace is computed from the authentication that was used for getting the OAuth2 Access Token. |
Codes retour
| 200 | Complete transactions response |
| 204 | No content. |
| 400 | Invalid status value |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 404 | Not found, no request available. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 503 | Service unavailable. |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.6.2/consents
consents
Résumé
Forwarding the PSU consent (AISP)
Description
### Description
In the mixed detailed consent on accounts
– the AISP captures the consent of the PSU
– then it forwards this consent to the ASPSP
This consent replaces any prior consent that was previously sent by the AISP.
### Prerequisites
– The TPP was registered by the Registration Authority for the AISP role.
– The TPP and the PSU have a contract that was enrolled by the ASPSP – At this step, the ASPSP has delivered an OAUTH2 « Authorization Code » or « Resource Owner Password » access token to the TPP (cf. § 3.4.2).
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) if any.
– The ASPSP takes into account the access token that establishes the link between the PSU and the AISP.
Business Flow
The PSU specifies to the AISP which of his/her accounts will be accessible and which functionalities should be available.
The AISP forwards these settings to the ASPSP.
The ASPSP answers by HTTP201 return code.
Scopes
- pisp
- cbpii
- aisp
- extended_transaction_history
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| access (required) | Access body List of consents granted to the AISP by the PSU. |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 201 | Created |
| 400 | Invalid status value |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 501 | Not Implemented. This code should be used when the entry point is implemented but cannot provide a result, given the context. When the entry point is not implemented at all, HTTP400 will be returned. |
| 503 | Service unavailable. |
Entrées
application/json
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.6.2/end-user-identity
endUserIdentity
Résumé
Retrieval of the identity of the end-user (AISP)
Description
Description
This call returns the identity of the PSU (end-user).
### Prerequisites
– The TPP was registered by the Registration Authority for the AISP role.
– The TPP and the PSU have a contract that was enrolled by the ASPSP – At this step, the ASPSP has delivered an OAUTH2 « Authorization Code » or « Resource Owner Password » access token to the TPP (cf. § 3.4.2).
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) if any.
– The ASPSP takes into account the access token that establishes the link between the PSU and the AISP.
Business Flow The AISP asks for the identity of the PSU. The ASPSP answers with the identity, i.e. first and last names of the end-user.
Scopes
- aisp
- cbpii
- extended_transaction_history
- pisp
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 200 | The ASPSP returns the identity of the PSU |
| 204 | No content. |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 404 | Not found, no request available. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 429 | Too many requests. |
| 500 | Internal server error. |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.6.2/funds-confirmations
fundsConfirmations
Résumé
Payment coverage check request (CBPII)
Description
Description
The CBPII can ask an ASPSP to check if a given amount can be covered by the liquidity that is available on a PSU cash account or payment card.
### Prerequisites
– The TPP was registered by the Registration Authority for the CBPII role
– The TPP and the PSU have a contract that was registered by the ASPSP – At this step, the ASPSP has delivered an « Authorization Code », a « Resource Owner Password » or a « Client Credential » OAUTH2 access token to the TPP (cf. § 3.4.2). – Each ASPSP has to implement either the « Authorization Code »/ »Resource Owner Password » or the « Client Credential » OAUTH2 access token model. – Doing this, it will edit the [security] section on this path in order to specify which model it has chosen
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP has presented its OAUTH2 « Authorization Code », « Resource Owner Password » or « Client Credential » access token which allows the ASPSP to identify the relevant PSU.
Business flow
The CBPII requests the ASPSP for a payment coverage check against either a bank account or a card primary identifier.
This request cannot handle exchange rate and must be specified with the relevant account currency.
The ASPSP answers with a structure embedding the original request and the result as a Boolean.
Scopes
- pisp
- cbpii
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| paymentCoverage (required) | PaymentCoverageRequestResource body parameters of a payment coverage request |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 200 | payment coverage request |
| 400 | Invalid status value |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 503 | Service unavailable. |
Entrées
application/json
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.6.2/payment-requests/{paymentRequestResourceId}/confirmation
paymentRequestConfirmation
Résumé
Confirmation of a payment request using an OAUTH2 Authorization code grant (PISP)
Description
Description
The PISP confirms one of the following requests or modifications:
– payment request on behalf of a merchant
– transfer request on behalf of the account’s owner
– standing-order request on behalf of the account’s owner
The ASPSP answers with a status of the relevant request and the subsequent Credit Transfer. ### Prerequisites
– The TPP was registered by the Registration Authority for the PISP role
– The TPP was provided with an OAUTH2 « Client Credential » access token by the ASPSP (cf. § 3.4.2).
– The TPP has previously posted a Request which was saved by the ASPSP (cf. § 4.5.3) – The ASPSP has answered with a location link to the saved Payment Request (cf. § 4.5.4) – The TPP has retrieved the saved request in order to get the relevant resource Ids (cf. § 4.6).
– The PSU was authenticated by the ASPSP through an OAUTH2 authorization code grant flow (REDIRECT approach) and the PISP got the relevant token
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP has presented its « OAUTH2 Authorization Code » access token Business flow
Once the PSU was authenticated through an OAUTH2 authorization code grant flow (REDIRECT approach), it is the due to the PISP to confirm the Request to the ASPSP in order to complete the process flow.
The ASPSP must wait for confirmation before executing the subsequent Credit Tranfer.
Any further confirmation by the PISP on the same Payment-Request must be ignored.
Scopes
- cbpii
- pisp
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| paymentRequestResourceId (required) | string path Identification of the Payment Request Resource |
| confirmationRequest (required) | ConfirmationResource body Parameters needed for confirmation of the Payment Request. Even though there is no parameter, a Json (void) body structure must be provided. |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 200 | retrieval of the Payment Request enriched with the status report |
| 400 | Invalid status value |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 409 | Conflict. The request could not be completed due to a conflict with the current state of the target resource. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 503 | Service unavailable. |
Entrées
application/json
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.6.2/payment-requests/{paymentRequestResourceId}
paymentRequest
Résumé
Cancellation of a Payment/Transfer Request (PISP)
Description
Description
The PISP sent a Payment/Transfer Request through a POST command.
The ASPSP registered the Payment/Transfer Request, updated if necessary the relevant identifiers in order to avoid duplicates and returned the location of the updated Request.
The PISP got the Payment/Transfer Request that was updated with the resource identifiers, and eventually the status of the Payment/Transfer Request and the status of the subsequent credit transfer.
The PISP requests for the payment cancellation (global cancellation) or for some payment instructions cancellation (partial cancellation)
No other modification of the Payment/Transfer Request is allowed.
### Prerequisites
– The TPP was registered by the Registration Authority for the PISP role
– The TPP was provided with an OAUTH2 « Client Credential » access token by the ASPSP (cf. § 3.4.2).
– The TPP previously posted a Payment/Transfer Request which was saved by the ASPSP (cf. § 4.5.3) – The ASPSP answered with a location link to the saved Payment/Transfer Request (cf. § 4.5.4) – The PISP retrieved the saved Payment/Transfer Request (cf. § 4.5.4)
– The TPP and the ASPSP successfully processed a mutual check and authentication
– The TPP presented its « OAUTH2 Client Credential » access token.
– The TPP presented the payment/transfer request.
– The PSU was successfully authenticated. Business flow
# Payment/Transfer request cancellation circumstances
The cancellation of a Payment/Transfer request might be triggered by the PISP upon request of the PSU.
It can also be triggered by the PISP itself in case of error or fraud detection.
Since the consequence of the cancellation will be a rejection of the Payment/Transfer request globally or limited to some of its instructions, the modification of the payment request will focus on setting the relevant status to the value « CANC ».
This « CANC » status must however be explained through a reason code that can be set with the following values: | Reason | description |
| —— | ———– |
| DS02 | The PSU himsef/herself ordered the cancellation. |
| DUPL | The PISP requested the cancellation for a duplication of a previous Payment/Transfer request |
| FRAD | The PISP requested the cancellation for fraudulent origin of the Payment/Transfer request |
| TECH | The PISP requested the cancellation for a technical issue on its side | #### Payment/Transfer request cancellation level
– Case of a payment with multiple instructions or a standing order, the PISP asks to cancel the whole Payment/Transfer or Standing Order Request including all non-executed payment instructions by setting the [paymentInformationStatus] and the relevant [statusReasonInformation] at payment level.
– Case of a payment with multiple instructions, the PISP asks to cancel one or several payment instructions by setting the [transactionStatus] and the relevant [statusReasonInformation] at each relevant instruction level. The cancellation request might need a PSU authentication before committing, especially when the request is PSU-driven. In other cases, the ASPSP may consider that a PSU authentication is irrelevant.
In order to meet all possibilities, the cancellation request must nevertheless include:
– The specification of the authentication approaches that are supported by the PISP (any combination of « REDIRECT » and « DECOUPLED » values).
– In case of possible REDIRECT or DECOUPLED authentication approach, one or two call-back URLs to be used by the ASPSP at the finalisation of the authentication and consent process : – The first call-back URL will be called by the ASPSP if the Transfer Request is processed without any error or rejection by the PSU – The second call-back URL is to be used by the ASPSP in case of processing error or rejection by the PSU. Since this second URL is optional, the PISP might not provide it. In this case, the ASPSP will use the same URL for any processing result. – Both call-back URLS must be used in a TLS-secured request.
– In case of possible « DECOUPLED » approach, a PSU identifier that can be processed by the ASPSP for PSU recognition. – The ASPSP saves the updated Payment/Transfer Request and answers to the PISP. The answer embeds – The specification of the chosen authentication approach taking into account both the PISP and the PSU capabilities. – In case of chosen REDIRECT authentication approach, the URL to be used by the PISP for redirecting the PSU in order to perform an authentication. Case of the PSU neither gives nor denies his/her consent, the Cancellation Request shall expire and is then rejected to the PISP. The expiration delay is specified by each ASPSP.
If any modification of the payment request other than cancellation is applied by the PISP, the ASPSP must reject the request with HTTP403 without modifying the payment request resource. There is no need for the PISP to post a confirmation of the cancellation request.
Scopes
- cbpii
- pisp
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| paymentRequestResourceId (required) | string path Identification of the Payment Request Resource |
| paymentRequest (required) | PaymentRequestResource body ISO20022 based payment Initiation Request |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 200 | The cancellation request was saved. The ASPSP may have to authenticate the PSU before committing the update. |
| 400 | Invalid status value |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 404 | Not found, no request available. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 409 | Conflict. The request could not be completed due to a conflict with the current state of the target resource. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 503 | Service unavailable. |
Entrées
application/json
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.6.2/payment-requests/{paymentRequestResourceId}/transactions
paymentRequestTransactions
Résumé
Retrieval of the Credit Transfert Transactions that were processed for a given payment request (PISP)
Description
Description
The PISP gets the execution history of a payment request.
This entry-point is an alternative to the retrieval of the history through the retrieval of the payment request.
So, each ASPSP may choose or not to implement this entry-point. Prerequisites
– The TPP was registered by the Registration Authority for the PISP role
– The TPP has previously posted a Standing Order Request which was saved by the ASPSP (cf. § 4.5.3) – The ASPSP has answered with a location link to the saved Payment Request (cf. § 4.5.4) – The TPP has retrieved the saved request in order to get the relevant resource Ids (cf. § 4.6).
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP was provided with an OAUTH2 « Client Credential » access token by the ASPSP (cf. § 3.4.2).
– The TPP presented its « OAUTH2 Client Credential » access token. Business flow
The PISP post the history request.
The ASPSP answers with the list of relevant transactions.
Scopes
- cbpii
- pisp
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| paymentRequestResourceId (required) | string path Identification of the Payment Request Resource |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 200 | retrieval of the Payment Request enriched with the status report |
| 400 | Invalid status value |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 409 | Conflict. The request could not be completed due to a conflict with the current state of the target resource. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 503 | Service unavailable. |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.6.2/payment-requests/{paymentRequestResourceId}
paymentRequests
Résumé
Retrieval of a payment request (PISP)
Description
Description
The following use cases can be applied:
– retrieval of a payment request on behalf of a merchant
– retrieval of a transfer request on behalf of the account’s owner
– retrieval of a standing-order request on behalf of the account’s owner The PISP has previously sent a Request through a POST command.
– The ASPSP has registered the Request, updated if necessary the relevant identifiers in order to avoid duplicates and returned the location of the updated Request.
– The PISP gets the Request that was updated with the resource identifiers, and eventually the status of the Payment/Transfer Request and the status of the subsequent credit transfer. ### Prerequisites
– The TPP was registered by the Registration Authority for the PISP role
– The TPP was provided with an OAUTH2 « Client Credential » access token by the ASPSP (cf. § 3.4.2).
– The TPP has previously posted a Request which was saved by the ASPSP (cf. § 4.5.3) – The ASPSP has answered with a location link to the saved Payment/Transfer Request (cf. § 4.5.4)
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP has presented its « OAUTH2 Client Credential » access token ### Business flow
The PISP asks to retrieve the Payment/Transfer Request that was saved by the ASPSP. The PISP uses the location link provided by the ASPSP in response of the posting of this request.
The ASPSP returns the previously posted Payment/Transfer Request which is enriched with:
– The resource identifiers given by the ASPSP
– The status information of the Payment Request and of the subsequent credit transfer
The status information must be available during at least 30 calendar days after the posting of the Payment Request. However, the ASPSP may increase this availability duration, based on its own rules.
Scopes
- cbpii
- pisp
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| paymentRequestResourceId (required) | string path Identification of the Payment Request Resource |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
Codes retour
| 200 | Retrieval of the previously posted Payment Request |
| 400 | Invalid status value |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 404 | Not found, no request available. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 503 | Service unavailable. |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.6.2/payment-requests
paymentRequests
Résumé
Payment request initiation (PISP)
Description
### Description
The following use cases can be applied:
– payment request on behalf of a merchant
– transfer request on behalf of the account’s owner
– standing-order request on behalf of the account’s owner
#### Data content
A payment request or a transfer request might embed several payment instructions having
– one single execution date or multiple execution dates – case of one single execution date, this date must be set at the payment level – case of multiple execution dates, those dates must be set at each payment instruction level
– one single beneficiary or multiple beneficiaries – case of one single beneficiary, this beneficiary must be set at the payment level – case of multiple beneficiaries, those beneficiaries must be set at each payment instruction level
Having at the same time multiple beneficiaries and multiple execution date might not be a relevant business case, although it is technically allowed.
Each implementation will have to specify which business use cases are actually supported.
A standing order request must embed one single payment instruction and must address one single beneficiary.
– The beneficiary must be set at the payment level
– The standing order specific characteristics (start date, periodicity…) must be set at the instruction level Payment request can rely for execution on different payment instruments:
– SEPA Credit Transfer (SCT)
– Domestic Credit Transfer in a non-Euro-currency
– International payment
The following table indicates how to use the different fields, depending on the payment instrument: | Structure | SEPA payments | Domestic payments in non-euro currency | International payments |
| ——— | ————- | ————————————– | ———————- |
| PaymentTypeInformation/InstructionPriority (payment level) | « HIGH » for high-priority SCT, « NORM » for other SCT, Ignored for SCTInst | « HIGH » for high-priority CT, « NORM » or ignored for other CT | « HIGH » for high-priority payments, « NORM » or ignored for other payments |
| PaymentTypeInformation/ServiceLevel (payment level) | « SEPA » for SCT and SCTInst | ignored | ignored |
| PaymentTypeInformation/CategoryPurpose (payment level) | « CASH » for transfer request, « DVPM » for payment request on behalf of a merchant || « CORT » for generic international payments, « INTC » for transfers between two branches within the same company, « TREA » for treasury transfers |
| PaymentTypeInformation/LocalInstrument (payment level) | « INST » pour les SCTInst, otherwise ignored | Ignored or valued with ISO20022 external code ||
| RequestedExecutionDate (at transaction level) | Optional. if set by the PISP, it indicates the date on debit on the ordering party account. If not set by the PISP, this requests the ASPSP to execute the payment instruction as soon as possible. |||
| EndToEndIdentification (at transaction level) | Mandatory | Optional ||
| UltimateDebtor (at transaction level) | Optional |||
| UltimateCreditor (at transaction level) | Optional |||
| InstructedAmount (at transaction level) | Mandatory || Mandatory and exclusive use of one of these structures |
| EquivalentAmount (at transaction level) | Not used || Mandatory and exclusive use of one of these structures |
| ChargeBearer (at transaction level) | « SLEV » for SCT and SCTInst | « SLEV » or « SHAR » | « CRED », « DEBT » or « SHAR » |
| Purpose (at transaction level) | Optional |||
| RegulatoryReportingCode (at transaction level) | Not used | Mandatory (possibly multiple values) |
| InstructionForCreditorAgent (at transaction level) | Not used || Optional (possibly multiple values) |
| RemittanceInformation | Mandatory. Structured or unstructured, depending on the local rules and constraints |||
| Debtor (at payment level) | Mandatory, 2 address lines only | Mandatory, 4 address lines only | Mandatory. Complete strustured address can be used. |
| DebtorAccount (at payment level) | Optional | Optional. Account currency may be specified ||
| DebtorAgent (at payment level) | Optional |||
| Creditor (at transaction level) | Mandatory, 2 address lines only | Mandatory, 4 address lines only | Mandatory. Complete strustured address can be used. Date and place of birth must be specified |
| CreditorAccount (at transaction level) | Mandatory | Mandatory. Account currency may be specified ||
| CreditorAgent (at transaction level) | Optional |||
| ClearingSystemId et ClearingSystemMemberId (at transaction level) | Not used || Optional |
| IntermediaryAgent et IntermediaryAgentAccount (at transaction level) | Not used | Optional || #### Prerequisites for all use cases
– The TPP was registered by the Registration Authority for the PISP role
– The TPP was provided with an OAUTH2 « Client Credential » access token by the ASPSP (cf. § 3.4.2).
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP has presented its « OAUTH2 Client Credential » access token # Business flow
## Payment Request use case
The PISP forwards a payment request on behalf of a merchant.
The PSU buys some goods or services on an e-commerce website held by a merchant. Among other payment method, the merchant suggests the use of a PISP service. As there is obviously a contract between the merchant and the PISP, there is no need for the ASPSP to check the existence of such a contract between the PSU and this PISP to initiate the process.
Case of the PSU that chooses to use the PISP service:
– The merchant forwards the requested payment characteristics to the PISP and redirects the PSU to the PISP portal.
– The PISP requests from the PSU which ASPSP will be used.
– The PISP prepares the Payment Request and sends this request to the ASPSP.
– The Request can embed several payment instructions having different requested execution date.
– The beneficiary, as being the merchant, is set at the payment level. ##### Transfer Request use case The PISP forwards a transfer request on behalf of the owner of the account. – The PSU provides the PISP with all information needed for the transfer. – The PISP prepares the Transfer Request and sends this request to the relevant ASPSP that holds the debtor account. – The Request can embed several payment instructions having different beneficiaries. – The requested execution date, as being the same for all instructions, is set at the payment level. ##### Standing Order Request use case The PISP forwards a Standing Order request on behalf of the owner of the account. – The PSU provides the PISP with all information needed for the Standing Order. – The PISP prepares the Standing Order Request and sends this request to the relevant ASPSP that holds the debtor account. – The Request embeds one single payment instruction with – The requested execution date of the first occurrence – The requested execution frequency of the payment in order to compute further execution dates – An execution rule to handle cases when the computed execution dates cannot be processed (e.g. bank holydays) – An optional end date for closing the standing Order
Scopes
- pisp
- cbpii
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| paymentRequest (required) | PaymentRequestResource body ISO20022 based payment Initiation Request |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
| ui_locales | string query End-User’s preferred languages and scripts for the user interface, represented as a space-separated list of BCP47 [RFC5646] language tag values, ordered by preference. |
| PSU-Workspace | string header Workspace to be used for processing the PSU authentication when confirming a PISP request. |
Codes retour
| 201 | The request was created as a resource. The ASPSP must authenticate the PSU. |
| 400 | Invalid status value |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 408 | Request Timeout. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 503 | Service unavailable. |
Entrées
application/json
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
/stet/psd2/v1.6.2/trusted-beneficiaries
trustedBeneficiaries
Résumé
Retrieval of the trusted beneficiaries list (AISP)
Description
Description
This call returns all trusted beneficiaries that were set by the PSU.
Those beneficiaries can benefit from an SCA exemption during payment initiation.
The result may be subject to pagination (i.e. retrieving a partial result in case of having too many results) through a set of pages by the ASPSP. Thereafter, the AISP may ask for the first, next, previous or last page of results.
Prerequisites
– The TPP was registered by the Registration Authority for the AISP role.
– The TPP and the PSU have a contract that was enrolled by the ASPSP – At this step, the ASPSP has delivered an OAUTH2 « Authorization Code » or « Resource Owner Password » access token to the TPP (cf. § 3.4.2).
– The TPP and the ASPSP have successfully processed a mutual check and authentication
– The TPP has presented its OAUTH2 « Authorization Code » or « Resource Owner Password » access token which allows the ASPSP to identify the relevant PSU and retrieve the linked PSU context (cf. § 3.4.2) if any.
– The ASPSP takes into account the access token that establishes the link between the PSU and the AISP.
### Business Flow
The AISP asks for the trusted beneficiaries list.
The ASPSP answers with a list of beneficiary details structure.
Scopes
- pisp
- cbpii
- aisp
- extended_transaction_history
Paramètres
| Authorization (required) | string header Access token to be passed as a header |
| PSU-IP-Address | string header IP address used by the PSU’s terminal when connecting to the TPP |
| PSU-IP-Port | string header IP port used by the PSU’s terminal when connecting to the TPP |
| PSU-HTTP-Method | string header Http method for the most relevant PSU’s terminal request to the TTP |
| PSU-Date | string header Timestamp of the most relevant PSU’s terminal request to the TTP |
| PSU-GEO-Location | string header Geographical location of the PSU as provided by the PSU mobile terminal if any to the TPP |
| PSU-User-Agent | string header « User-Agent » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Referer | string header « Referer » header field sent by the PSU terminal when connecting to the TPP. Notice that an initial typo in RFC 1945 specifies that « referer » (incorrect spelling) is to be used. The correct spelling « referrer » can be used but might not be understood. |
| PSU-Accept | string header « Accept » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Charset | string header « Accept-Charset » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Encoding | string header « Accept-Encoding » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Accept-Language | string header « Accept-Language » header field sent by the PSU terminal when connecting to the TPP |
| PSU-Device-ID | string header UUID (Universally Unique Identifier) for a device, which is used by the PSU, if available. UUID identifies either a device or a device dependant application installation. In case of installation identification this ID need to be unaltered until removal from device. |
| Digest | string header Digest of the body |
| Signature (required) | string header [http-signature of the request](https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) The keyId must specify the way to get the relevant qualified certificate. It is requested that this identifier is an URL aiming to provide the relevant Qualified Certificate. |
| X-Request-ID (required) | string header Correlation header to be set in a request and retrieved in the relevant response |
| workspace | string query Workspace to be used for processing an AISP request. If not provided, the default workspace is computed from the authentication that was used for getting the OAuth2 Access Token. |
Codes retour
| 200 | The ASPSP returns the list of whitelisted beneficiaries |
| 204 | No content. |
| 401 | Unauthorized, authentication failure. |
| 403 | Forbidden, authentication successful but access to resource is not allowed. |
| 404 | Not found, no request available. |
| 405 | Method Not Allowed. |
| 406 | Not Acceptable. |
| 429 | Too many requests. |
| 500 | Internal server error. |
| 501 | Not Implemented. This code should be used when the entry point is implemented but cannot provide a result, given the context. When the entry point is not implemented at all, HTTP400 will be returned. |
Sorties
application/hal+json; charset=utf-8
application/json; charset=utf-8
Authentifications disponibles
OAuth 2.0
Catégories
-
STETPSD2 V1.4.0
-
STETPSD2V142
-
STETPSD2V162
- get accountsBalances
- get accounts
- get accountsOverdrafts
- get accountsOwners
- get accountsTransactionsDetails
- get accountsTransactions
- put consents
- get endUserIdentity
- post fundsConfirmations
- post paymentRequestConfirmation
- put paymentRequest
- get paymentRequestTransactions
- get paymentRequests
- post paymentRequests
- get trustedBeneficiaries
-
Cas d'usage
-
Comment tester l'API
Vérifiez la disponibilité des fonds
Ce service permet de vérifier la disponibilité des fonds pour le compte de notre client pour un montant donné d’une transaction.
Prérequis
Pour procéder à cette requête il est nécessaire de remplir les prérequis d’éligibilité, d’avoir récupéré le jeton d’accès OAUTH2 (voir le cas d’usage « Récupérez votre jeton« ) et de fournir les paramètres du body.
Requête
POST /funds-confirmations
Paramètres obligatoires du body requis pour l’appel de ce service
- paymentCoverageRequestId : Identifiant de la requête de paiement
- instructedAmount : La structure comprenant le montant renseigné ainsi que la devise
- currency : Devise du montant renseigné
- amount : Montant qui permettra de déterminer si les fonds sont disponibles
- accountId : Identifiant unique pour le compte renseigné
- iban : Numéro de compte bancaire international (IBAN)
Réponse
Le résultat retourné reprendra les informations de la requête ainsi que la réponse concernant la disponibilité des fonds sous la forme d’un booléen.
Un lien self sera également présent pour revenir à la page obtenue juste après exécution de la requête .
Exemple
Requête
POST /v1/funds-confirmations
Body
{
« paymentCoverageRequestId » : « MyCoverage123456 »,
« instructedAmount » : {
« currency » : « EUR »,
« amount » : « 12345 » },
« accountId » : { « iban » : « YY13RDHN98392489481620896668799742 » }
}
}
Résultat
Status code : 200
Body
{
« request » : {
« paymentCoverageRequestId » : « MyCoverage123456 »,
« instructedAmount » : {
« currency » : « EUR »,
« amount » : « 12345 » },
« accountId » : {« iban » : « YY13RDHN98392489481620896668799742 » }
},
« result » : true,
« _links » : {
« self » : {
« href » : « v1/funds-confirmations »
}
}
}
Console Try-it
Principe
En vous connectant sur le portail BPCE API, vous pouvez :
- Faire appel à l’API « disponibilité des fonds » via un formulaire dans lequel vous sélectionnez votre application et le jeton d’accès
- Saisir les paramètres de la méthode « POST /funds-confirmations » que vous souhaitez tester (soit headers, soit body), ceux mentionnés par une étoile étant obligatoires
Une fois les paramètres saisis, vous pouvez lancer l’exécution de la requête : vous obtiendrez soit un résultat, soit une erreur.
Les données utilisées pour faire le test en Try-it sont issues de personas (voir la rubrique « Comment tester l’API ? » > « Tester nos personas »).
Version 1.4.2
A compter du 8 juillet 2020, le try-it ne sera possible que pour la version V1.4.2.
Si vous avez déjà effectué une demande de GoLive, vous devez alors créer une nouvelle application, puis sélectionner la nouvelle API STET V1.4.2.
Si vous n’avez PAS effectué de demande de GoLive, vous pouvez :
- soit modifier votre application existante pour l’associer à la nouvelle API STET V1.4.2.
- soit créer une nouvelle application, puis sélectionner la nouvelle API STET V1.4.2.
Paramètres du Try-it pour la méthode « POST /funds-confirmations »
Pour les paramètres de type de données « body », il est possible de copier-coller les exemples (partie gauche de l’écran) dans le formulaire (à droite de l’écran) en changeant juste les valeurs spécifiques au client choisi.
| Paramètre | Description | Type de données | Type de paramètre | Obligatoire |
| Authorization | Jeton d’accès devant être fourni comme header | Chaîne de caractères | Header | Oui |
| PSU-IP-Address | Adresse IP utilisés par le client connecté sur votre application
(*) Donnée obligatoire si le client est connecté ou non renseignée en cas d’accès batch |
Chaîne de caractères | Header | Non* |
| PSU-IP-Port | Port IP du terminal utilisé par le client connecté sur votre application | Chaîne de caractères | Header | Non |
| PSU-HTTP-Method | Méthode http utilisée pour la requête du client | Chaîne de caractères | Header | Non |
| PSU-Date | Timestamp utilisé par la requête du client | Chaîne de caractères | Header | Non |
| PSU-GEO-Location | Localisation géographique que le client vous a fournie via son terminal si elle est disponible | Chaîne de caractères | Header | Non |
| PSU-User-Agent | Header « User-Agent » envoyé par le terminal du client connecté à votre application | Chaîne de caractères | Header | Non |
| PSU-Referer | Header « Referer » envoyée par le terminal du client connecté à votre application. Il est à noter que dans des spécifications antérieures des RFC 1945, on préconise le nom « referer » (mal orthographié). Le nom « referrer » peut être utilisé au risque de ne pas être compris. | Chaîne de caractères | Header | Non |
| PSU-Accept | Header « Accept » envoyé par le terminal du client connecté à votre application | Chaîne de caractères | Header | Non |
| PSU-Accept-Charset | Header « Accept-Charset » envoyé par le terminal du client connecté à votre application. | Chaîne de caractères | Header | Non |
| PSU-Accept-Encoding | Header « Accept-Encoding » envoyé par le terminal du client connecté à votre application. | Chaîne de caractères | Header | Non |
| PSU-Accept-Language | Header « Accept-Language » envoyé par le terminal du client connecté à votre application. | Chaîne de caractères | Header | Non |
| Digest | Synthèse du body | Chaîne de caractères | Header | Non |
| Signature | Signature http de la requête (voir https://datatracker.ietf.org/doc/draft-cavage-http-signatures/) La partie keyId du header devrait avoir le format suivant keiId= »SN=XXX,CA=YYYYYYYYYYYYYYYY » où « XXX » est le numéro de série en hexadécimal sans aucun préfixe (comme 0x, du certificat QSEAL dont la clé privée a servi pour la signature de celui-ci
« YYYYYYYYYYYYYYYY » est l’émetteur DN, nom complet de l’autorité de certification ayant émis ce certificat HTTP400 et qui sera renvoyé par le serveur dans le cas d’une signature invalide ou absente. |
Chaîne de caractères | Header | Oui |
| X-Request-ID | Header de corrélation à paramétrer dans la requête et devant être récupéré dans la réponse de celle-ci | Chaîne de caractères | Header | Oui |
Assemblage Sandbox
Principe
La sandbox BPCE API peut être utilisée de 2 manières :
- Via le Try-it du portail BPCE-API (se référer au cas d’utilisation « Console Try-it »)
- Directement via votre application en appelant l’API « disponibilité des fonds » de la plateforme BPCE-API : c’est le mode assemblage sandbox illustré ci-dessous et qui sera disponible sous peu.

Explications
En assemblage sandbox, il y a 2 appels :
- Le premier pour récupérer le jeton d’autorisation
- Le second pour faire l’appel à l’API d »‘information sur compte »
Votre application consommatrice de l’API « Disponibilité des fonds » de la sandbox va devoir récupérer un jeton d’accès via sa clé d’authentification auprès de l’AS (Authentification Server). Ainsi l’application pourra consommer la méthode « POST /funds-confirmations » grâce à son jeton d’accès.
Les données utilisées pour faire les tests seront issues des persona (voir le cas d’utilisation « Testez nos persona »), ce qui vous permettra de choisir des profils spécifiques de façon à mieux cibler vos tests.
Tester nos personas
Conformément à la réglementation DSP2 (cf. RTS Art. 30 (5)), nous devons, en tant qu’ASPSP, mettre à disposition un dispositif d’essai comprenant une assistance et permettant des tests de connexion et de fonctionnement afin que les TPP qui ont demandé l’agrément nécessaire puissent tester les logiciels et applications qu’ils utilisent pour proposer un service de paiement aux utilisateurs.
Il est aussi demandé l’utilisation de données fictives. C’est l’objectif de ces données de tests sous forme de « persona » qui rassemblent divers clients sur base de :
- segment de clientèle (étudiant, actif, retraité, entrepreneur individuel, etc..) ;
- caractéristiques de leurs comptes (mono-compte, multi-comptes, solde qui est statique) ;
- le consentement PSU a déjà été donné ;
- données utiles attendues en entrée par les API (identifiant banque à distance, IBAN).
Ce jeu de données évoluera au cours du temps avec rajout de données additionnelles (autres clients, nombre de transactions, profondeur d’historique). Revenez régulièrement sur cette section pour être à jour !
Les identifiants et données ci-dessous sont des données fictives et ne peuvent pas être utilisées en production.
Personas
 |
 |
| LEA SANDBOXA | CLAIRE RECETTEB |
| Etudiante 1 seul compte de paiement (abonné PART) | Actif et entrepreneur individuel 2 comptes de paiement PART et un PRO/EI (abonné PART) |
 |
 |
| GEORGES PERSONAC | GILLES TESTUNID |
| Actif1 seul compte joint de paiementMr OU Mme (abonné PART)200 transactions disponibles surl’IBAN FR7617515000920400085945890 | Retraité3 comptes de paiement PART (abonné PART) : Mr, Mr OU Mme, Mr ET Mme |
NB : pour tous ces personas, il vous faudra saisir le code SMS = « 12345678 » dans l’écran d’authentification proposé en mode assemblage.
ATTENTION : NOUVEAUX IDENTIFIANTS
| Persona | Segment | Nouvel Identifiant | Codetab | IBAN | Détenteur | Consentement :Solde /Transactions /Identité | Solde | Devise |
| LEA SANDBOXA | Particulier | 9999999901 | 17515 | FR7617515000920400430518020 | Mme LEA SANDBOXA | TRUE TRUE FALSE | -150.00 | EUR |
| CLAIRE RECETTEB | Particulier | 9999999902 | 17515 | FR7617515900000400358074026 | Mme CLAIRE RECETTEB | TRUE TRUE FALSE | 0.00 | EUR |
| CLAIRE RECETTEB | Entrepreneur individuel | 9999999902 | 17515 | FR7617515900000800358074006 | Mme CLAIRE RECETTEB | TRUE TRUE FALSE | +23766.98 | EUR |
| GEORGES PERSONAC | Particulier | 9999999903 | 17515 | FR7617515000920400085945890 | Mr et Mme GEORGES PERSONAC | TRUE TRUE FALSE | +10.00 | EUR |
| GILLES TESTUNID | Particulier | 9999999904 | 17515 | FR7617515000920440878790811 | Mr GILLES TESTUNID | TRUE TRUE FALSE | +11880.30 | EUR |
| GILLES TESTUNID | Particulier | 9999999904 | 17515 | FR7617515000920402428687756 | Mr OU Mme GILLES TESTUNID | TRUE TRUE FALSE | 0.00 | EUR |
| GILLES TESTUNID | Particulier | 9999999905 | 17515 | FR7617515000920402428748381 | Mr ET Mme GILLES TESTUNID | TRUE TRUE FALSE | +5879.22 | EUR |
Utiliser le fallback
Principe
Conformément à la réglementation, les établissements du groupe BPCE ont mis en place une interface dédiée aux prestataires de services de paiement : il s’agit des API REST DSP2 publiées.
Si les API DSP2 exposées sont défaillantes, le prestataire des services de paiement pourra utiliser la solution couvrant les « mesures d’urgence applicables à une interface dédiée » (ou « fallback ») dont le principe est le suivant :
Cette solution répond aux exigences réglementaires de la DSP2 (article 33 des RTS). Vous pourrez l’utiliser avec les mêmes conditions et prérequis décrits dans la rubrique « Eligibilité« .
Roadmap
Retrouvez ci-dessous les éléments de notre trajectoire prévisionnelle :
| Version | Fonctionnalités | Sandbox
Date de déploiement BPCE API Dev Portal & Sandbox |
Live
Date de déploiement BPCE Live API Gateway |
| v1.0 | Fallback (*) | Non applicable | Fin Septembre 2019 |
(*) Fonctionnalités Principales :
- Utilisation par le TPP du même endpoint que l’interface dédiée. Il dépend donc du code établissement qui permet d’adresser le bon référentiel client. La liste de nos établissements et les valeurs possibles sont précisées dans la rubrique « Limitations« .
- Un paramètre de requête (header « fallback:1 » présent ou absent) ajouté par le TPP permet de distinguer une requête « fallback » d’une requête API via l’interface dédiée qui doit être utilisée systématiquement
- Authentification du TPP via authentification mutuelle TLS par un certificat eIDAS (QWAC)
- Sécurisation identique à celle d’un accès à la banque en ligne du PSU (même interface utilisée par le PSU qu’en accès direct, et mêmes moyens d’authentification du client)
- Dans le cadre de la montée en charge de l’usage de l’interface dédiée (API), il n’est pas mis en place de bascule dynamique : la solution fallback est toujours active
- La solution de fallback est une solution de secours ne devant pas être utilisée comme moyen principal d’accès pour proposer les services DSP2. Son usage en est monitoré et tout usage abusif par un/des TPP sera automatiquement reporté auprès de l’autorité nationale compétente.
Exemple
1. Dans le cas où les API DPS2 sont indisponible de façon imprévue ou le système tomberait en panne (voir critères dans le texte RTS Art. 33), le TPP peut alors envoyer la requête :
POST https://www.<codetab>.oba-bad-me-live.api.89c3.com/stet/psd2/oauth/token (nouvelle url à prendre en compte dès à présent)
(Pour rappel, l’url 89C3 existante www.<codetab>.live.api.89C3.com ne sera plus disponible à partir du 28/09/2025)
avec <codetab> =
- 17515 pour Caisse d’Epargne
avec :
- son certificat eIDAS QWAC de production
- le paramètre header (fallback: »1″)
2. Si les vérifications sont positives, l’url de redirection (permettant d’afficher la page d’accès à la banque en ligne) et le jeton JWT seront dans le header de la répoonse
3. Le TPP doit utiliser ensuite les identifiants du PSU via sa méthode propriétaire
Pour plus de détails sur la requête POST, voir STET V1.4.0.47 / Part I / section 3.4.3.2 / page 22
Limites
Les contraintes de cette solution sont les suivantes :
- Pas de réutilisation du contexte de l’interface dédiée, ni du jeton d’accès valable 180 jours (AISP)
- L’identifiant du terminal accédant (TermId) doit être obligatoirement fourni, sinon l’accès aux pages d’identification/authentification sera bloqué
- Seules les fonctionnalités DSP2 présentes sur la banque en ligne (référence : banque à distance sur internet fixe – pas la banque sur mobile) sont accessibles via le fallback. Par exemple, les services de banque en ligne ne proposent pas de paiement e-commerce. Cette fonctionnalité PISP n’est donc pas disponible en mode fallback.
- Le client utilisateur des services (PSU) doit être connecté à l’app du TPP (pas de possibilité de traitement batch AISP pour venir récupérer les données consenties du client). La DSP2 imposant également un renforcement des moyens d’authentification forte (AF/SCA) systématique pour les accès à la banque à distance/en ligne, les moyens d’authentification fournis aux clients PSU seront utilisés (liste non exhaustive) :
- Soft token
- OTP SMS
- Clé physique (pour les entreprises)
Historique des versions
Cette API REST est conforme à la spécification interbancaire française STET (https://www.stet.eu/en/psd2/) afin de répondre aux exigences réglementaires de la DSP2. Voir la section « limitations » pour prendre connaissance des limitations fonctionnelles.
Pour rappel :
- les textes de la directive de paiement numéro 2 (DSP2, référence UE 2015/2366 du 25/11/2015) sont rentrés en application le 13 janvier 2018 : http://eur-lex.europa.eu/legal-content/FR/TXT/?uri=CELEX:32015L2366
- ils ont été complétés par les normes techniques de réglementation (NTR, règlement délégué UE 2018/389) relatives à l’authentification forte du client et à des normes ouvertes communes et sécurisées de communication dont la date d’application se situe au 14 septembre 2019. Ces normes sont les RTS (Rules Technical Standards) : https://eur-lex.europa.eu/legal-content/FR/TXT/?toc=OJ%3AL%3A2018%3A069%3ATOC&uri=uriserv%3AOJ.L_.2018.069.01.0023.01.FRA
En France, l’ordonnance n° 2017-1252 du 9 août 2017 transpose la directive DSP2 dans la partie législative du code monétaire et financier. L’ordonnance est complétée au plan réglementaire par les décrets n° 2017-1313 et n° 2017-1314 du 31 août 2017 et les cinq arrêtés du 31 août 2017.
Planning des évolutions à venir de l’API
Conformément à l’article 30 (5) des RTS, une assistance pour les prestataires PSP tiers est mise à disposition. Ce support est accessible via le formulaire sur ce portail BPCE API, ou via https://www.api.89c3.com/fr/nous-contacter. Les réponses se font pendant les heures de travail ouvrées.
Le principe général du support est schématisé ci-dessous en prenant en compte les délais réglementaires prévus à l’article 30 (4) des RTS :

Versionning de l’API
| NOS VERSIONS API | VERSION NORME STET |
| v1 | v1.4.0.47 |
| v1.4.2 | v1.4.2.17 |
| v1.6.2 | v1.6.2.0 |
Evolutions importantes apportées depuis la dernière version livrée
| CAS D’USAGE / MÉTHODE(S) | DATE D’EFFET | DESCRIPTION DE L’ÉVOLUTION |
| rajout de la V1.4.2 | 31 mai 2022 | Documentation portail |
| rajout de la V1.6.2 | 31 novembre 2022 | Documentation portail |
Roadmap
Politique de décommissionnement des versions de l’API
La politique du décommissionnement (= arrêt d’une version d’une API sur les environnements de production et sandbox) est fonction du cycle de vie des API, et il est prévu une phase de tuilage entre deux versions majeures d’API comme indiqué dans le schéma ci-dessous :

La communication du décommissionnement d’une version N se fera à la date de déploiement de la version N+1. Le canal de communication privilégié est le portail BPCE API dans la partie « Roadmap » de l’API impactée. Une communication via courriel vers les correspondants des prestataires enrôlés sur le portail BPCE API pourra venir compléter ce dispositif.
Planning des évolutions fonctionnelles à venir de l’API
Cette API fait l’objet d’améliorations et d’évolutions continues. L’article 30 (4) des RTS précise que des changements significatifs de l’API peuvent intervenir sans délai. Nous appliquons cette clause dans les cas suivants :
- problème bloquant impactant de façon généralisée au moins l’un des segments de clients majeur (particuliers, professionnels, entreprises),
- problème de sécurité,
- évolutions demandées par les autorités nationales compétentes pour répondre à la trajectoire réglementaire.
Retrouvez ci-dessous les éléments de notre trajectoire prévisionnelle :
| Version de
l’API |
Fonctionnalités | Date de déploiement
BPCE API Dev Portal |
Date de déploiement
BPCE Live API Gateway |
Date de
décommissonnement |
| v1.0 | Disponibilité des fonds (*) | 14 mars 2019 | 14 septembre 2019 | 30 juin 2023 |
| v1.4.2 | Disponibilité des fonds (*) | 24 septembre 2020 | 31 juin 2021 | non encore annoncée |
| v1.6.2 | Disponibilité des fonds (*) | 16 novembre 2022 | 28 février 2023 | non encore annoncée |
(*) Fonctionnalités Principales :
- Obtention de l’information demandée sous forme OUI/NON ;
- Pas de blocage des fonds par le teneur de compte ;
- Pas de différence entre les versions V1 et V1.4.2 et V1.6.2
Limitations
Limitations fonctionnelles
Les limitations de cette API DSP2 sont les suivantes :
- Ne s’applique qu’aux comptes de paiements en euros, éligibles (non bloqué ou sous séquestre) et accessibles en ligne (cf. texte de la Directive DSP2) et consentement PSU fourni
- Ne couvre que les segments des particuliers (compte de dépôt) et professionnels/entrepreneurs individuels (compte courant). A terme, d’autres segments clients seront disponibles
- N’utilise que le mode d’authentification par redirection (Authentification Forte du client demandée et gérée via la banque)
- Ne permet l’accès que via l’IBAN du compte de paiement (et non via l’identifiant de l’instrument de paiement)
Accès aux données de production
Pour accéder aux données réelles, veuillez utiliser auparavant notre API ‘Register ».
Comme en mode test, le code établissement (voir ci-dessous) vous permettra d’adresser le bon référentiel client via un point d’accès au format :
www.<cdetab>.oba-bad-me-live.api.89c3.com (nouvelle url à prendre en compte dès à présent)
(Pour rappel, l’url 89C3 existante www.<codetab>.live.api.89C3.com ne sera plus disponible à partir du 28/09/2025)
Exemples :
- STET V1.4.0 POST https://www.17515.oba-bad-me-live.api.89c3.com/stet/psd2/v1/funds-confirmations ( /!\ scope = piisp )
- STET V1.4.2 POST https://www.17515.oba-bad-me-live.api.89c3.com/stet/psd2/v1.4.2/funds-confirmations ( /!\ scope = cbpii )
- STET V1.6.2 POST https://www.17515.oba-bad-me-live.api.89c3.com/stet/psd2/v1.6.2/funds-confirmations ( /!\ scope = cbpii )
| Codetab | Nom de l’établissement | Nom abrégé |
| 11315 | Caisse d’Epargne Provence Alpes Corse | CEPAC |
| 11425 | Caisse d’Epargne Normandie | CEN |
| 12135 | Caisse d’Epargne Bourgogne Franche-Comté | CEBFC |
| 14445 | Caisse d’Epargne Bretagne-Pays De Loire | CEBPL |
| 13135 | Caisse d’Epargne Midi-Pyrénées | CEMP |
| 13335 | Caisse d’Epargne Aquitaine Poitou-Charentes | CEAPC |
| 13485 | Caisse d’Epargne Languedoc-Roussillon | CELR |
| 13825 | Caisse d’Epargne Rhône Alpes | CERA |
| 14265 | Caisse d’Epargne Loire Drôme Ardèche | CELDA |
| 14505 | Caisse d’Epargne Loire-Centre | CELC |
| 17515 | Caisse d’Epargne Ile De France | CEIDF |
| 18315 | Caisse d’Epargne Côte d’Azur | CECAZ |
| 18715 | Caisse d’Epargne Auvergne et Limousin | CEPAL |
| 15135 | Caisse d’Epargne Grand Est Europe | CEGEE |
| 16275 | Caisse d’Epargne Hauts de France | CEHDF |
Eligibilité
Les ressources de l’API « Initiation de paiements » ne peuvent être consommées que par des PSP ayant le rôle de Prestataires de Services d’initiation de Paiement (PISP). Ce statut est délivré par les autorités financières du pays dans lequel la demande est effectuée ; en France il s’agit de l’Autorité de Contrôle Prudentiel et de Résolution (ACPR), liée à la Banque de France.
L’obtention et la conservation d’un agrément relèvent de procédures rigoureuses afin d’apporter des garanties fortes aux utilisateurs des services de paiements, les formulaires étant disponibles sur le site de l’ACPR : https://acpr.banque-france.fr/autoriser/procedures-secteur-banque/tous-les-formulaires.
Une fois l’agrément donné, le format de cet identifiant (Organisation Identifier = OID) fourni par l’autorité compétente est :
PSDXX-YYYYYYYY-ZZZZZZZZ:
XX =>code ISO 3166 du pays de l’autorité compétente hyphen-minus « – » (0x2D (ASCII), U+002D (UTF-8))YYYYYYYY => 2-8 caractères du l’identifiant de l’autorité compétente (A-Z, pas de séparateur)hyphen-minus « – » (0x2D (ASCII), U+002D (UTF-8))ZZZZZZZZ => identifiant du PSP spécifié par l’autorité nationale compétente (sans restriction sur le nombre – ou sur le type – de caractère utilisé)
Cet identifiant OID est important à 2 titres :
- il servira à vous identifier lors des appels dans les requêtes des API STET (via le paramètre « client_id »)
- il devra être présent dans les certificats eIDAS que vous fournirez au teneur de compte (voir ci-dessous)
De plus, vous devez disposer de certificats délivrés par une autorité de certification reconnue (Qualified Certification Service Providers – QTSP: https://webgate.ec.europa.eu/tl-browser/#/) conformes au règlement eIDAS (electronic IDentification And trust Services : https://www.ssi.gouv.fr/entreprise/reglementation/confiance-numerique/le-reglement-eidas/) et respectant la norme ETSI (https://www.etsi.org/deliver/etsi_ts/119400_119499/119495/01.02.01_60/ts_119495v010201p.pdf).
Afin de consommer les API DSP2 proposées sur ce portail, le TPP doit enrôler son app et nous transmettre via notre API Register des certificats de production signés par une autorité de certification agréée :
- un premier jeu de certificats QWAC (pour l’authentification mutuelle TLS) et QSEALC (à charger sur notre passerelle via l’API Register) pour la sandbox
- un autre jeu de certificats QWAC (pour l’authentification mutuelle TLS) et QSEALC (à charger sur notre passerelle via l’API Register) pour la production
NB IMPORTANT : en cas de renouvellement de certificat, et si l’autorité de certification (QTSP) est différente (ou c’est la même entreprise QTSP mais qui utilise des clés racines différentes), le TPP doit avertir le support API disponible via ce site de 2 mois avant à toutes fins de vérifier que les élements de la nouvelle autorité de certification sont bien chargés sur nos infrastuctures.
Un identifiant keyID devra aussi être fourni dans un format conforme à la spécification STET intégrant une empreinte SHA256 après le caractère « _ » char, voir exemple dans la documentation STET Part 3 / Interaction Examples : keyId=https://path.to/myQsealCertificate_612b4c7d103074b29e4c1ece1ef40bc575c0a87e.
Seules les clés publiques au format .pem sont nécessaires. Des contrôles sur les données des certificats seront effectués à partir des registres Français (REGAFI : https://www.regafi.fr) et Européen (ABE ou EBA : https://euclid.eba.europa.eu/register/pir/disclaimer).
Catégories
-
Cas d'usage
-
Comment tester l'API