Caisse d’Epargne – PSD2 Funds Availability (STET Standard V1.4.2/1.6.2)
How to reduce your risk ?
You, as a Third Party Provider (TPP), delivered to a customer a private labeled payment card linked to his bank account. The customer (PSU) is performing a transaction on an e-commerce site with it. The customer has previously given a consent to your entity as well as to his bank account holder.
Using API “Funds availability” setup by banks (ASPSP), you can request for real-time transaction amount coverage data authorized by the customer without asking for online banking credentials. You can then reduce your risk for overdue payments.
The bank will respond yes or no without any funds blockage corresponding to the transaction amount, neither any validation of this transaction.
The API resources can only be consumed if you have obtained the Card Based Payment Instrument Issuer (“CBPII” or “PIISP”) role status. This prerequisite is described in section “Eligibility”.
Once done, the overall process is as follows :
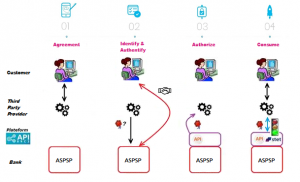
1- The customer agreed to use your service. He needs to select his ASPSP through your interface.
2- During the first set of data exchanges, you will request for an authorization token (and a refresh one). For this CBPII role, you need these tokens BEFORE consuming API resources. These tokens are issued by the ASPSP AFTER an identification and authorization process of the bank accound holder.
The ASPSP will :
- check your certificates and on-going agreement delivered by the Comptent Authority ;
- identify and authorize the customer using the “redirect” mode in order to issue the tokens.
3- If the above access is granted by the customer, you can then get these OAUTH2 tokens thru secure exchanges (see use case “Get your token“).
4- Whenever you present this token to the BPCE API gateway, you will be able to consume this API resources (see use case “Check funds availability“).
If the regulated 180-day token validity period expires, this process needs to be started again (see use case “Refresh your token“).
NB : any ASPSP can refuse the access to customer’s data fo rany justified reason (non compliant API call, blocked account, …).
Regulatory publications
| Period | Document |
| Availability of DSP2 APIs to date | Load the document |
| Statistics Q1 2025 | Load the document |
| Statistics Q4 2024 | Load the document |
| Statistics Q3 2024 | Load the document |
| Statistics Q2 2024 | Load the document |
| Statistics Q1 2024 | Load the document |
| Statistics Q4 2023 | Load the document |
| Statistics Q3 2023 | Load the document |
| Statistics Q2 2023 | Load the document |
| Statistics Q1 2023 | Load the document |
| Statistics Q4 2022 | Load the document |
| Statistics Q3 2022 | Load the document |
| Statistics Q2 2022 | Load the document |
| Statistics Q1 2022 | Load the document |
| Statistics Q4 2021 | Load the document |
| Statistics Q3 2021 | Load the document |
| Statistics Q2 2021 | Load the document |
| Statistics Q1 2021 | Load the document |
| Statistics Q4 2020 | Load the document |
| Statistics Q3 2020 | Load the document |
| Statistics Q2 2020 | Load the document |
| Statistics Q1 2020 | Load the document |
Catégories
-
Technical use cases
Get your token
Access to PSD2 API is granted by the bank with an authorization token (or access token) issued using OAUTH2 standardized process.
How it works ?
See also STET V1.4.2.17 / Part I / section 3.4

1. The customer (PSU) provides the identity of the bank which holds his accounts (ASPSP) to the TPP.
2. The TPP initiates an OAUTH2 access token request sequence by redirecting the customer to the ASPSP’s authorization infrastructure using GET /authorize
See also STET V1.4.2.17 / Part I / section 3.4 1
3- ASPSP will :
- Identify and authenticate the PSU
- Check your role and validity of your eIDAS certificates and agreement
4- Once checks are done and correct, ASPS will redirect the PSU to your site using “call-back” URL given in the GET /authorize and to ASPSP for the Go Live process.
You will find in the response of this request a one-time-token with a short life period.
5- You can then call the ASPSP in order to request the OAUTH2 token (and refresh one) using POST /token with previously received data (incl’d the one-time-token).
Note : these /token requests for getting the Authorization Code flow shall be sent WITHOUT the « scope » parameter.
See also STET V1.4.2.17 / Part I / section 3.4
6- ASPSP will :
- Check your role and validity of your eIDAS certificates and agreement
- Checks the direct or indirect matching between the Authorization Number within the eIDAS certificate and the [client_id] value
7- Once checks are done and correct, ASPSP returns a response HTTP200 (OK) with data including the access token.
See also see STET V1.4.2.17 / Part I / section 3.4
8- As soon as you get the OAUTH2 access token (and a 180-day valid refresh token) issued by the bank, you can use it for each API request within the “Authorization” header, prefixed by the token type “Bearer”.
The [client_id] that is linked to the access token must directly or indirectly match with the Authorisation Number that is located within the TPP’s eIDAS certificate (QWAC).
If the access token is expired, the request will be rejected with HTTP401 with an error equal to “invalid_token”.
The request can be replayed once the access token has been refreshed suing the use case “Refresh your token“.
If your refresh token is about to expire, you will have to perform again all this process, meaning also redirect to ASPSP for customer’s strong autentication (PSU SCA).
For more details, see also OAUTH 2.0 Authorization Framework : https://tools.ietf.org/html/rfc6749#section-4.1
Example
You can find an example of this request in section “Test our API” and then “Use our sandbox“
Check funds availability
This service allows you to check if customer has enough funds available on his payment bank account (linked to your payment card based intrument) to cover the current transaction.
Prerequisites
In order to proceed, TPP needs to fulfill all eligibility criteria and to present a valid OAUTH2 Authorization token (see use case “Get your token“).
Request
post /funds-confirmations
see STET V1.4.0 / Part II / section 4.6.4 page 23
Mandatory parameters
paymentCoverageRequestId : Id for the request
payee : merchant
instructedAmount : amount and currency of the transaction
accountId : Unique Id for the customer’s account
Result
The result given by the ASPSP is a boolean (YES or NO).
Example
Request
Post http://localhost:8080/v1/funds-confirmations
Body
{
“paymentCoverageRequestId” : “MyCoverage123456”,
“instructedAmount” : {
“currency” : “EUR”,
“amount” : “12345” },
“accountId” : { “iban” : “YY13RDHN98392489481620896668799742” }
}
}
Résultat
Status code : 200
Body
{
“request” : {
“paymentCoverageRequestId” : “MyCoverage123456”,
“instructedAmount” : {
“currency” : “EUR”,
“amount” : “12345” },
“accountId” : {“iban” : “YY13RDHN98392489481620896668799742” }
},
“result” : true,
“_links” : {
“self” : {
“href” : “v1/funds-confirmations”
}
}
}
see also STET V1.4.0 / Part III / section 6 page 12
Acceptance tests
The purpose of these tests is to ensure that the API complies with the STET standard. They should be validated before any application deployment.
| Description | Test data |
| Nominal case (funds are available) | PSU Persona : CLAIRE
Scope OAuth2 = piisp Amount < 459€ accountId :FR7617515900000800358074006 Currency : EUR Result :
|
| Insufficient funds | PSU Persona : LEA
Prérequis : scope OAuth2 = piisp Amount > 4 179€ accountId : FR7613807008043001965405158 Currency : EUR Result :
|
| Non authorized HTTP request using GET method | PSU Persona : LEA
Scope OAuth2 = piisp Result : HTTP code 405 => unauthorized method |
| HTTP request with missing IBAN | PSU Persona : LEA
Scope OAuth2 = piisp Amount = 4 179€ accountId : FR7617515000920400430518020 Currency : EUR Result : HTTP code 400 => wrong request |
| HTTP request with missing amount parameter | PSU Persona : LEA
Scope OAuth2 = piisp accountId : FR7617515000920400430518020 Result : HTTP code 400 => wrong request |
| HTTP request with missing of incorrect currency | PSU Persona : CLAIRE
Scope OAuth2 = piisp Amount > 4 179€ accountId : FR7617515900000800358074006 Currency : USD Result : HTTP code 400 => wrong request |
| HTTP request with a missing or incorrect transaction Id | PSU Persona : LEA
Scope OAuth2 = piisp Amount > 4 179€ Currency : EUR Result : HTTP code 400 => wrong request |
Refresh your token
Principle
The refresh token issued by the bank ASPSP is valid up to 180 days and needs to be renewed before it expires. Please also note that :
- Authorization and refresh tokens can be revoked at any moment ;
- If the Authorization token is revoked, then the refresh one is automatically revoked (and the other way round) ;
- The access token has a shorter life cycle (10 to 15min) on standalone device.
How it works ?
1. You request for a refresh token using POST /token
See also STET V1.4.0.47 / Part I / section 3.4.3.4 / page 25
2. ASPSP :
- Identifies and authenticates the TPP through the presented eIDAS certificate (QWAC)
- Checks the direct or indirect matching between the Authorization Number within the eIDAS certificate and the [client_id] value.
- Controls last PSU SCA date (< 180 jours).
3. If correct, ASPSP then answers through a HTTP200 (OK) that embeds a new autorization token and refresh token that can replace the previous one. You need to store safely these tokens.
4. ASPSP de facto revokes the previous refresh token :
- After timeout of the by-law specified delay between two SCAs ;
- After timeout of the ASPSP specified delay based on internal rules if any ;
- After reject of a request for insufficient scope in order to allow the AISP to request another token with the desired scope ;
- On request of a PSU wanting to revoke the TPP access on his/her account data.
Please also note that, as a TPP, you are able to ask for the revocation of the refresh token through a POST /revoke request.
See also STET V1.4.0 / Part I / section 3.4.3.5 / page 26
RFC 7009, cf. https://tools.ietf.org/html/rfc7009
Version history
This API is based on STET specifications in order to meet PSD2’s regulatory requirements. It takes into account the functional limitations specific to this ASPSP.

As a reminder
- payment services directive (PSD2, (UE) 2015/2366 of 25/11/2015) went into force on january 13, 2018:
- it is supplemented by regulatory technical standards for strong customer authentication (RTS, Commission Delegated Regulation (EU) No 2018/389) and common and secure open standards of communication that will apply on september14, 2019. These standards are called RTS (Rules Technical Standards) :
In France, the ordinance n° 2017-1252 of August 9, 2017 implements the PSD2 directive into the regulatory section of the monetary and financial code. This ordinance has been supplemented by two decrees (n° 2017-1313 and n° 2017-1314), and five orders that were published on August 31, 2017.
| Our API version | STET standard version |
| v1.0 | v1.4.0.47 |
| v1.4.2 | v1.4.2.17 |
| v1.6.2 | v1.6.2.0 |
You can also refer to the FAQ section and the virtual assistant about STET specifications.
Roadmap
This API can evolve. Please note that API modifications can occur out of the three-month regulatory notice period (art. 30 des RTS / paragraphe 4). We apply this in case of :
- urgent functional issue to solve impacting all PSU of at least one major customers segment
- security issue
- evolutions requested by the national competent authority
Please do find below our forecast roadmap :
| Our API versions | STET Standard versions | Features | Sandbox
Deployment date BPCE API Dev Portal & Sandbox |
Live
Deployment date BPCE Live API Gateway |
|
| v1.0 | v1.4.0.47 | Check funds availability | March 14, 2019 | September 14, 2019 | |
| v1.4.2 | v1.4.2.17 | Check funds availability | – | May 31, 2022 | |
| V1.6.2 | v1.6.2.0 | Check funds availability | march 14, 2029 | February 8, 2023 | – |
Deprecation process
According to API product life cycle, an API version can be deprecated (means this API is not any more accessible on gateways and sandbox). An overlap period between two major API releases is provided as described below :

The communication on the deprecation of a version N will be done at the release date of version N+1 through this portal / “roadmap” section.
Limits
Functional Limitation
The limitations of this PSD2 API are :
- Apply only to Caisse d’Epargne customers who suscribed online banking services
- Apply only to active and eligible online accessible payment accounts in euro currency
- Payment accounts from corporate segments are not yet available using this API
- Use the authentication with redirect only (Strong Customer Authentication required and handled by the bank APSPS)
- Acces to the customer’s informations will only be possible if he gave his consent previously
- Access to payment account is done only using IBAN as main parameter (and not your payment instrument)
- There will be no reservations of funds
Limitations on data
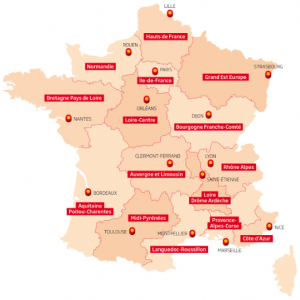
Live data will be accessible by using first our enrolment API “Register”.
The list of current available bank institutions for this API is detailed below.
Examples :
- STET V1.4.0 POST https://www.17515.oba-bad-me-live.api.89c3.com/stet/psd2/v1/funds-confirmations ( /!\ scope = piisp )
- STET V1.4.2 POST https://www.17515.oba-bad-me-live.api.89c3.com/stet/psd2/v1.4.2/funds-confirmations ( /!\ scope = cbpii )
- STET V1.6.2 POST https://www.17515.oba-bad-me-live.api.89c3.com/stet/psd2/v1.6.2/funds-confirmations ( /!\ scope = cbpii )
(new URL to be taken into account from now on)
(As a reminder, the existing URL www.<codetab>.live.api.89C3.com will no longer be available as of 28/09/2025)
The list of current available bank institutions for this API is detailed below. The parameter “codetab” will allow you to setup the right customer database thru a dedicated « endpoint » for each bank having the following format : www.codetab.live.api.89c3.com
| Codetab | Bank name | Bank short name |
| 11315 | Caisse d’Epargne Provence Alpes Corse | CEPAC |
| 11425 | Caisse d’Epargne Normandie | CEN |
| 12135 | Caisse d’Epargne Bourgogne Franche-Comté | CEBFC |
| 14445 | Caisse d’Epargne Bretagne-Pays De Loire | CEBPL |
| 13135 | Caisse d’Epargne Midi-Pyrénées | CEMP |
| 13335 | Caisse d’Epargne Aquitaine Poitou-Charentes | CEAPC |
| 13485 | Caisse d’Epargne Languedoc-Roussillon | CELR |
| 13825 | Caisse d’Epargne Rhône Alpes | CERA |
| 14265 | Caisse d’Epargne Loire Drôme Ardèche | CELDA |
| 14505 | Caisse d’Epargne Loire-Centre | CELC |
| 17515 | Caisse d’Epargne Ile De France | CEIDF |
| 18315 | Caisse d’Epargne Côte d’Azur | CECAZ |
| 18715 | Caisse d’Epargne Auvergne et Limousin | CEPAL |
| 15135 | Caisse d’Epargne Grand Est Europe | CEGEE |
| 16275 | Caisse d’Epargne Hauts de France | CEHDF |
Eligibility
The “Funds availability” API resources can only be used by Payment Service Providers (PSP) with a “Card Based Payment Instrument Issuer” role (CBPII or PIISP depending on used STET version).
In order to provide a service to users of payment services under PSD2 directive, you must be a licenced PSP such as credit institution, electronic money institution, and payment institution. This status is delivered by financial authorities of the country where the request is made ; in France it is the “Autorité de Contrôle Prudentiel et de Résolution” (ACPR), under the supervision of the Banque de France regulatory body.
Obtaining and maintaining an authorization requires rigorous procedures in order to give strong guarantees to the payment services users.
The forms are provided on the ACPR website : https://acpr.banque-france.fr/autoriser/procedures-secteur-banque/tous-les-formulaires.
Once the agrement is granted, the Organisation Identifier (OID) given by the national authority has the following format :
PSDXX-YYYYYYYY-ZZZZZZZZ
“PSD” as 3 character legal person identity type reference
2 character ISO 3166 country code representing the NCA country
2-8 character NCA identifier (A-Z uppercase only, no separator)
PSP identifier (authorization number as specified by NCA)
This OID is very important for :
- identify yourself as a TPP in the STET API requests using the parameter “client_ID”
- to be included into the eIDAS certificates to be delivered to the bank (see below)
You also need eIDAS (electronic IDentification And trust Services) compliant certificates delivered by a Qualified Certification Service Provider (QTSP, see list available on https://webgate.ec.europa.eu/tl-browser/#/).
In order to be able to consume PSD2 API published on our BPCE Portal, you have to forward us using .pem format :
- QWAC and et QSEALC live certificates for the sandbox (if available for this ASPSP)
- QWAC and et QSEALC live certificates for our BPCE API Live gateway
Please embed only public keys. Controls on other data will be based on European Banking Association TPP register (https://euclid.eba.europa.eu/register/pir/disclaimer).
You can also refer to the FAQ section and the chatbot about the principle of eligibility.
Catégories
-
Technical use cases

